42 Million Passwords – now that’s a big number, and the worst part – they aren’t even hashed. Nope, not at all – not even badly. Apparently the intrusion took place earlier this year, in January 2013 – but there was no public announcement.
The data was found on the same server where the hacked data from some other big heists was stored (Adobe/PR Newswire/NW3C etc). And to make it even worse, at least 10% of the users (which itself is over 4 million) use absolutely terrible passwords – passwords that would have been useless even if they were hashed.
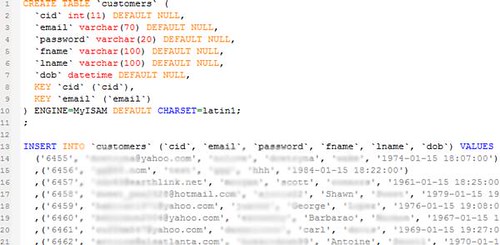
Image Source: Cupid Media Hack Exposed 42M Passwords
Almost 2 million of the users had the password ‘123456‘ followed by 1.2 million with ‘111111‘ (I’m guessing they had a 6 char minimum password requirement).
A hack on niche online dating service Cupid Media earlier this year has exposed names, e-mail addresses and—most notably—plain-text passwords for 42 million accounts, according to a published report.
The cache of personal information was found on the same servers that housed tens of millions of records stolen in separate hacks on sites including Adobe, PR Newswire, and the National White Collar Crime Center, KrebsonSecurity journalist Brian Krebs reported Tuesday night. An official with Southport, Australia-based Cupid Media told Krebs that user credentials appeared to be connected to “suspicious activity” that was detected in January. Officials believed they had notified all affected users, but they are in the process of double-checking that all affected accounts have had their passwords reset in light of Krebs’s discovery.
The compromise of 42 million passwords makes the episode one of the bigger passcode breaches on record. Adding to the magnitude is the revelation the data was in plaintext, instead of a cryptographically hashed format that requires an investment of time, skill, and computing power to crack.
Standing at 42 million passwords, it is indeed one of the biggest breaches ever – and whoever got hold of this had to put no time, effort or computing power into brute forcing hashes. They just opened the DB dump and had 42 million e-mail addresses and passwords.
With many people re-using their passwords across multiple sites, this is indeed like striking the lottery for hackers.
Back in 2011 when Canadian Dating Site PlentyofFish.com was Hacked, they exposed 30 million user accounts – so they weren’t far behind. Notice any similarities? Yah both dating sites…and both storing passwords in plain text.
Making matters worse, many of the Cupid Media users are precisely the kinds of people who might be receptive to content frequently advertised in spam messages, including male enhancement products, services for singles, and diet pills.
The Cupid Media user records reviewed by Krebs contain the usual assortment of weak passwords. More than 1.9 million accounts were protected by 123456. Another 1.2 million used 111111. Users who used the same e-mail address and password to secure accounts on other sites are vulnerable to hijacking. Word of the Cupid Media compromise follows recent reports of password leaks from a host other sites or companies, including Adobe (150 million reversibly encrypted passwords), MacRumors forums (860,000), and web software developer vBulletin (number not disclosed).
Ars has long advised readers to use a password manager that stores a long, randomly generated password that’s unique for every important site. That way, when breaches hit a particular site, users are left scrambling to change credentials for other accounts that used the same password.
You can read more here too:
– Cupid Media Hack Exposed 42M Passwords
– 42 million passwords exposed following massive dating website hack
Once again, another good reason to use PassPack/LastPass/KeePass etc. It once again reinforces the fact that reusing passwords is a terrible idea, especially when sites like this still exist in 2013 that store your password in plain text.
Source: Ars Technica
