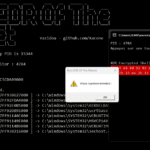
BestEDROfTheMarket is a naive user-mode EDR (Endpoint Detection and Response) tool designed to serve as a testing ground
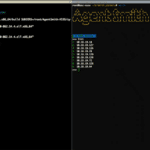
AgentSmith HIDS – Host Based Intrusion Detection
AgentSmith HIDS is a powerful component of a Host-based Intrusion Detection system, it has anti-rootkit functionalities and is a very performant way to collect information about a host.
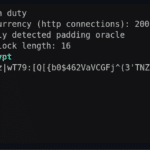
padre – Padding Oracle Attack Exploiter Tool
padre is an advanced exploiter and Padding Oracle attack tool that can be deployed against CBC mode encryption.
Privacy Implications of Web 3.0 and Darknets
The evolution of the internet has been rapid over the years and has impacted the privacy implications of Web 3.0 and Darknets
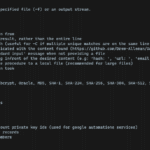
DataSurgeon – Extract Sensitive Information (PII) From Logs
DataSurgeon (ds) is a versatile tool designed to Extract Sensitive Information (PII) From Logs, it’s intended to be used for incident response, penetration testing, and CTF challenges.