p0wnedShell is an offensive PowerShell Runspace Post Exploitation host application written in C# that does not rely on powershell.exe but runs PowerShell commands and functions within a PowerShell run space environment (.NET). It has a lot of offensive PowerShell modules and binaries included making the process of Post Exploitation easier. What the author tried was […]
windows privilege escalation
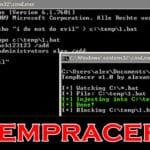
TempRacer – Windows Privilege Escalation Tool
TempRacer is a Windows Privilege Escalation Tool written in C# designed to automate the process of injecting user creation commands into batch files with administrator level privileges. The code itself is not using that many resources because it relies on callbacks from the OS. You can keep it running for the the whole day to […]
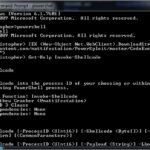
PowerSploit – A PowerShell Post-Exploitation Framework
PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an assessment. Basically, it is a PowerShell Post-Exploitation Framework that helps you with various tasks like DLL injection, invoking shellcode and setting up script persistence. It also includes reflective PE injection and can reflectively load […]
windows-privesc-check – Windows Privilege Escalation Scanner
Windows-privesc-check is standalone executable that runs on Windows systems. It tries to find misconfiguration that could allow local unprivileged users to escalate privileges to other users or to access local applications (e.g. databases). Essentially it’s a Windows privilege escalation scanner, the Microsoft side of the World counterpart to unix-privesc-check – which we wrote about a […]