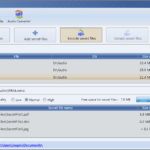
DeepSound is an audio steganography tool and audio converter that hides secret data into audio files, the application also enables you to extract secret files directly from audio files or audio CD tracks. This audio steganography tool can be used as copyright marking software for wave, flac, wma, ape, and audio CD. DeepSound also support […]
steganography
OpenPuff – Professional Steganography Tool
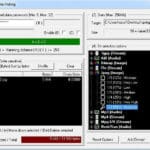
OpenPuff is a professional steganography tool, with unique features you won’t find among any other free or commercial software. OpenPuff is 100% free and suitable for highly sensitive data covert transmission. The tool contains deniable steganography, carrier chains, unique layers of security and obfuscation, multiple carrier formats, is portable and is freeware (ad-free). Features of […]
spectrology – Basic Audio Steganography Tool
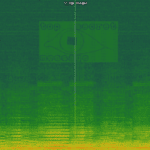
spectrology is a Python-based audio steganography tool that can convert images to audio files with a corresponding spectrogram encoding, this allows you to hide hidden messages via images inside audio files. Using this tool you can select range of frequencies to be used and all popular image codecs are supported. Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
usage: spectrology.py [-h] [-o OUTPUT] [-b BOTTOM] [-t TOP] [-p PIXELS] [-s SAMPLING] INPUT positional arguments: INPUT Name of the image to be converted. optional arguments: -h, --help show this help message and exit -o OUTPUT, --output OUTPUT Name of the output wav file. Default value: out.wav). -b BOTTOM, --bottom BOTTOM Bottom frequency range. Default value: 200. -t TOP, --top TOP Top frequency range. Default value: 20000. -p PIXELS, --pixels PIXELS Pixels per second. Default value: 30. -s SAMPLING, --sampling SAMPLING Sampling rate. Default value: 44100. |
Example
|
1 |
python spectrology.py test.bmp -b 13000 -t 19000 |
You […]
StegExpose – Steganalysis Tool For Detecting Steganography In Images
StegExpose is a steganalysis tool specialized in detecting steganography in lossless images such as PNG and BMP (LSB – least significant bit type). It has a command line interface and is designed to analyse images in bulk while providing reporting capabilities and customization which is comprehensible for non forensic experts. Steganography is the art or […]