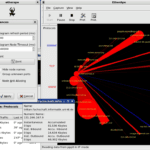
EtherApe is a graphical network monitor for Unix modelled after etherman. Featuring link layer, IP and TCP modes, it displays network activity graphically. Hosts and links change in size with traffic. Colour coded protocols display. It supports Ethernet, FDDI, Token Ring, ISDN, PPP, SLIP and WLAN devices, plus several encapsulation formats. It can filter traffic […]
network-monitoring
PBNJ – Network Architecture Monitoring Tool
[ad] PBNJ is a suite of tools to monitor changes on a network over time. It does this by checking for changes on the target machine(s), which includes the details about the services running on them as well as the service state. PBNJ parses the data from a scan and stores it in a database. […]
argus – Auditing Network Activity – Performance & Status Monitoring
[ad] Another tool for the security side, good for forensics, monitoring and auditing. Argus is a fixed-model Real Time Flow Monitor designed to track and report on the status and performance of all network transactions seen in a data network traffic stream. Argus provides a common data format for reporting flow metrics such as connectivity, […]
IPAudit – Network Activity Monitor with Web Interface
[ad] IPAudit monitors network activity on a network by host, protocol and port. It listens to a network device in promiscuous mode, and records every connection between two ip addresses. A unique connection is determined by the ip addresses of the two machines, the protocol used between them, and the port numbers (if they are […]
Driftnet – View Images From Live Network Traffic
[ad] Inspired by EtherPEG, Driftnet is a program which listens to network traffic and picks out images from TCP streams it observes. Fun to run on a host which sees lots of web traffic. EtherPEG was a program that sniffed for JPEGs passing by on the AirPort networks at MacHack, and showed them on the […]