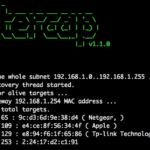
BetterCAP is a powerful, modular, portable MiTM framework that allows you to perform various types of Man-In-The-Middle attacks against the network. It can also help to manipulate HTTP and HTTPS traffic in real-time and much more. BetterCap has some pretty impressive Spoofing abilities with multiple host discovery (just launch the tool and it will start […]
mitm
MITMf – Man-In-The-Middle Attack Tool
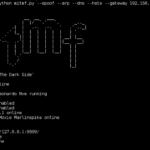
MITMf is a Man-In-The-Middle Attack Tool which aims to provide a one-stop-shop for Man-In-The-Middle (MiTM) and network attacks while updating and improving existing attacks and techniques. Originally built to address the significant shortcomings of other tools (e.g Ettercap, Mallory), it’s been almost completely re-written from scratch to provide a modular and easily extendible framework that […]
Google Revoking Trust In CNNIC Issued Certificates
So another digital certificate fiasco, once again involving China from CNNIC (no surprise there) – this time via Egypt. Google is going to remove all CNNIC and EV CAs from their products, probably with the next version of Chrome that gets pushed out. As of yet, no action has been taken by Firefox – or […]
Viber Vulnerable To Man In The Middle Attack (MITM)
So this week, researchers at the University of New Haven have been focusing on Viber and have found that pretty much everything transferred and stored on the Viber service, except the messages themselves is not encrypted either in transit or at rest (doodles, images, location data & videos). The implication of this is that the […]
Hackers Get Hold Of Wildcard Google SSL Certificate – Could Hijack Gmail Accounts
One of the big discussions points this week is about a wildcard cert for Google that has leaked out from a Dutch company called DigiNotar. The certificate is good for all Google domains – it’s a *.google.com cert. This is bad news and apparently has been in the wild for a while, some people are […]