So unsurprisingly a security researcher found some cheap Android devices phoning home to China when buying a phone to travel with. One of the phones seems to be Blu R1 HD, which is ‘Currently unavailable’ on Amazon.com and customers that bought it have received security update e-mails. Security researchers have uncovered a secret backdoor in […]
malware
Android Malware Giving Phones a Hummer
So Android Malware has always been quite a problem, especially with it being so easy to install random .apk files and the proliferation of 3rd party app stores. Also so many people with rooted phones and the fact that software installed can root your phone and take complete control. The current worry is the Hummer […]
Cuckoo Sandbox – Automated Malware Analysis System
Cuckoo Sandbox is Open Source software for automating analysis of suspicious files. To do so it makes use of custom components that monitor the behaviour of the malicious processes while running in an isolated environment. In other words, you can throw any suspicious file at it and in a matter of seconds Cuckoo will provide […]
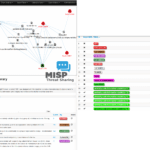
MISP – Malware Information Sharing Platform
MISP, Malware Information Sharing Platform and Threat Sharing, is an open source software solution for collecting, storing, distributing and sharing cyber security indicators and threat about cyber security incidents analysis and malware analysis. MISP is designed by and for incident analysts, security and ICT professionals or malware reverser to support their day-to-day operations to share […]
Twitter Patents Technique To Detect Mobile Malware
So it was discovered that Twitter has been granted a patent which covers detection of mobile malware on websites to protect its user base. The patent was filed back in 2012, but well – as we know these things take time. The method is something like the technology Google uses in Chrome to warn you […]