Bluto is a Python-based tool for DNS recon, DNS zone transfer testing, DNS wild card checks, DNS brute forcing, e-mail enumeration and more. The target domain is queried for MX and NS records. Sub-domains are passively gathered via NetCraft. The target domain NS records are each queried for potential Zone Transfers. If none of them […]
dns
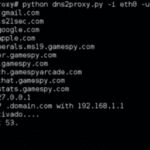
dns2proxy – Offensive DNS server
dns2proxy is an offensive DNS server that offers various features for post-exploitation once you’ve changed the DNS server of a victim. It’s very frequently used in combination with sslstrip. Features Traditional DNS Spoofing Implements DNS Spoofing via Forwarding Detects and corrects changes for sslstrip to work Usage Using the spoof.cfg config file with the format: […]
dnsteal – DNS Exfiltration Tool
dnsteal is a DNS exfiltration tool, essentially a fake DNS server that allows you to stealthily extract files from a victim machine through DNS requests. dnsteal is coded in Python and is available on Github. Features dnsteal currently has: Support for multiple files Gzip compression supported Supports the customisation of subdomains Customise bytes per subdomain […]
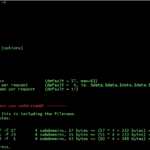
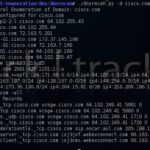
DNSRecon – DNS Enumeration Script
DNSRecon is a Python based DNS enumeration script designed to help you audit your DNS security and configuration as part of information gathering stage of a pen-test. DNS reconnaissance is an important step when mapping out domain resources, sub-domains, e-mail servers and so on and can often lead to you finding an old DNS entry […]
Rackspace Recovers From Major DNS DDoS
So Rackspace has just recovered from a major DNS DDoS attack which rendered some domains inaccessible for over 11 hours. It seems to have been a fairly frequent occurrence lately with Namecheap also undergoing several attacks against its DNS infrastructure. I got affected again recently on December 18th when they were hit with a massive […]