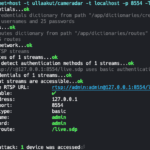
Cameradar is a Go-based tool to hack RTSP Video Surveillance CCTV Cameras, it can detect open RTSP hosts, detect device models and launch automated attacks. The main features of Cameradar are: Detect open RTSP hosts on any accessible target host Detect which device model is streaming Launch automated dictionary attacks to get their stream route […]
dSploit APK Download – Hacking & Security Toolkit For Android
dSploit APK Download is a Hacking & Security Toolkit For Android which can conduct network analysis and penetration testing activities. It aims to offer to IT security experts the most complete and advanced professional toolkit to perform network security assessments on a mobile device. Once dSploit is started, you will be able to easily map […]
Scallion – GPU Based Onion Hash Generator
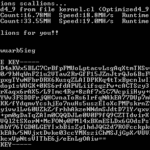
Scallion is a GPU-driven Onion Hash Generator written in C#, it lets you create vanity GPG keys and .onion addresses (for Tor’s hidden services) using OpenCL. Scallion runs on Mono (tested in Arch Linux) and .NET 3.5+ (tested on Windows 7 and Server 2008) Scallion was used to find collisions for every 32bit key id […]
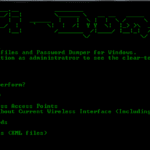
WiFi-Dumper – Dump WiFi Profiles and Cleartext Passwords
WiFi-Dumper is an open-source Python-based tool to dump WiFi profiles and cleartext passwords of the connected access points on a Windows machine. This tool will help you in a Wifi penetration testing and could also be useful when performing red team assessments or internal infrastructure engagements. Each option in the tool generates the “.txt” file […]
truffleHog – Search Git for High Entropy Strings with Commit History
truffleHog is a Python-based tool to search Git for high entropy strings, digging deep into commit history and branches. This is effective at finding secrets accidentally committed. truffleHog previously functioned by running entropy checks on git diffs. This functionality still exists, but high signal regex checks have been added, and the ability to surpress entropy […]