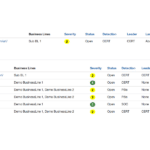
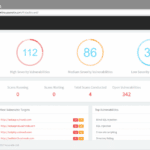
FIR (Fast Incident Response) is a cyber security incident management platform designed for agility and speed. It allows for easy creation, tracking, and reporting of cybersecurity incidents. In the fields of computer security and information technology, computer security incident management involves the monitoring and detection of security events on a computer or computer network, and […]
Countermeasures
maltrail – Malicious Traffic Detection System
Maltrail is a malicious traffic detection system, utilizing publicly available (black)lists containing malicious and/or generally suspicious trails, along with static trails compiled from various AV reports and custom user-defined lists, where trail can be anything from domain name (e.g. zvpprsensinaix.com for Banjori malware), URL (e.g. http://109.162.38.120/harsh02.exe for known malicious executable), IP address (e.g. 185.130.5.231 for […]
Massive Acunetix Online Update Brings New Features & UI
So there’s been a massive Acunetix Online update that has pushed out a brand new UI plus a whole bunch of new features and capabilities, including really powerful stuff for security professionals and organisations who take their security seriously The update has focused a lot on Usability of the UI and features for infosec pros […]
Microsoft Azure Web Application Firewall (WAF) Launched
Not too long after Amazon launched their cloud protection WAF the Microsoft Azure Web Application Firewall (WAF) has been made generally available in all public Azure DCs. It’s a good move with the majority of websites and services moving into one of the big 3 cloud providers (AWS, Google or Azure) and the vast majority […]
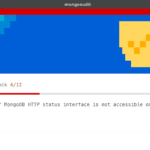
mongoaudit – MongoDB Auditing & Pen-testing Tool
mongoaudit is a CLI tool for MongoDB auditing of servers, detecting poor security settings and performing automated penetration testing. It is widely known that there are quite a few holes in MongoDB’s default configuration settings. This fact, combined with abundant lazy system administrators and developers, has led to what the press has called the MongoDB […]