tko-subs is a tool that helps you to detect & takeover subdomains with dead DNS records, this could be dangling CNAMEs point to hosting services or to nothing at all or NS records that are mistyped.
What does tko-subs – Detect & Takeover Subdomains With Dead DNS Records Do?
This tool allows you:
- To check whether a subdomain can be taken over because it has:
- a dangling CNAME pointing to a CMS provider (Heroku, Github, Shopify, Amazon S3, Amazon CloudFront, etc.) that can be taken over.
- a dangling CNAME pointing to a non-existent domain name
- one or more wrong/typoed NS records pointing to a nameserver that can be taken over by an attacker to gain control of the subdomain’s DNS records
- To actually take over those subdomain by providing a flag
-takeover. Currently, take over is only supported for Github Pages and Heroku Apps and by default the take over functionality is off. - To specify your own CMS providers and check for them via the providers-data.csv file. In that file, you would mention the CMS name, their CNAME value, their string that you want to look for and whether it only works over HTTP or not. Check it out for some examples.
How to install tko-subs to takeover subdomains with dead DNS records
You need GO installed. Once you have GO, just type go get github.com/anshumanbh/tko-subs to download the tool.
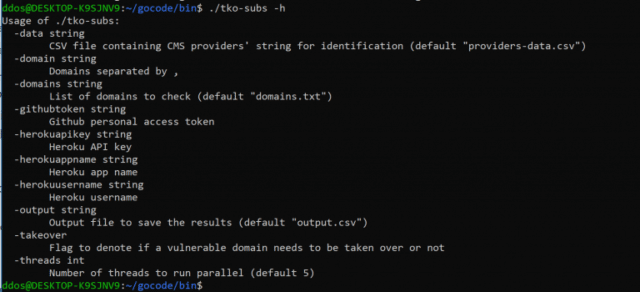
Once the tool is downloaded, type tko-subs -h.
The next thing we need to do is to get the following information:
- Github’s Personal Access Token – Make sure this token has the rights to create repositories, references, contents, etc. You can create this token here – https://github.com/settings/tokens
- Heroku Username and API key
- Heroku app name – You can create a static app on Heroku with whatever you want to be displayed on its homepage by following the instructions here – https://gist.github.com/wh1tney/2ad13aa5fbdd83f6a489. Once you create that app, use that app name in the flag (see below). We will use that app to take over the domain (with the dangling CNAME to another Heroku app).
NOTE – You only need these values if you want to take over subdomains. By default, that’s not required.
Required Go Packages to build.
|
1 2 3 4 5 6 7 |
go get github.com/bgentry/heroku-go go get github.com/gocarina/gocsv go get github.com/google/go-github/github go get github.com/olekukonko/tablewriter go get golang.org/x/net/publicsuffix go get golang.org/x/oauth2 go get github.com/miekg/dns |
You can download tko-subs here:
Or read more here.

randy says
hi