Quasar is a fast and light-weight Windows remote administration tool coded in C#. The usage ranges from user support through day-to-day administrative work to employee monitoring. It aims to provide high stability and an easy-to-use user interface and is a free, open source tool. Features of Quasar RAT Windows Remote Administration Tool The main features […]
Archives for May 2020
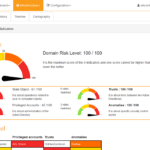
Pingcastle – Active Directory Security Assessment Tool
PingCastle is a Active Directory Security Assessment Tool designed to quickly assess the Active Directory security level with a methodology based on a risk assessment and maturity framework. It does not aim at a perfect evaluation but rather as an efficiency compromise. The risk level regarding Active Directory security has changed. Several vulnerabilities have been […]