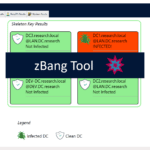
zBang is a risk assessment tool for Privileged Account Threat Detection on a scanned network, organizations and red teamers can utilize zBang to identify potential attack vectors and improve the security posture of the network. The results can be analyzed with the graphic interface or by reviewing the raw output files. The tool is built […]
Archives for March 2020
Memhunter – Automated Memory Resident Malware Detection
Memhunter is an Automated Memory Resident Malware Detection tool for the hunting of memory resident malware at scale, improving the threat hunter analysis process and remediation times. It’s a self contained binary that can be deployed and managed at scale, does not use memory dumps and relies purely on memory inspection to do its work. […]
Sandcastle – AWS S3 Bucket Enumeration Tool
Sandcastle is a Python-based Amazon AWS S3 Bucket Enumeration Tool, formerly known as bucketCrawler. The script takes a target’s name as the stem argument (e.g. shopify) and iterates through a file of bucket name permutations. Amazon S3 [Simple Storage Service] is cloud storage for the Internet. To upload your data (photos, videos, documents etc.), you […]