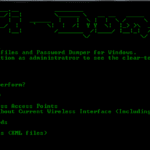
WiFi-Dumper is an open-source Python-based tool to dump WiFi profiles and cleartext passwords of the connected access points on a Windows machine. This tool will help you in a Wifi penetration testing and could also be useful when performing red team assessments or internal infrastructure engagements. Each option in the tool generates the “.txt” file […]
Archives for December 2019
truffleHog – Search Git for High Entropy Strings with Commit History
truffleHog is a Python-based tool to search Git for high entropy strings, digging deep into commit history and branches. This is effective at finding secrets accidentally committed. truffleHog previously functioned by running entropy checks on git diffs. This functionality still exists, but high signal regex checks have been added, and the ability to surpress entropy […]