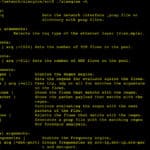
AIEngine is a next-generation interactive/programmable Python/Ruby/Java/Lua and Go AI-driven Network Intrusion Detection System engine with capabilities of learning without any human intervention, DNS domain classification, Spam detection, network collector, network forensics and many others. AIEngine also helps network/security professionals to identify traffic and develop signatures for use them on NIDS, Firewalls, Traffic classifiers and so […]
Archives for November 2019
Sooty – SOC Analyst All-In-One CLI Tool
Sooty is a tool developed with the task of aiding a SOC analyst to automate parts of their workflow and speed up their process. The main goal of Sooty is to perform as much of the routine checks as possible which allows the analyst more time to spend on deeper analysis. Features of Sooty SOC […]