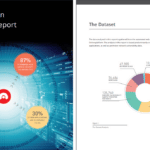
So what is wild on the web this year? Need to know about the most critical web vulnerabilities in 2019 to protect your organization? Well luckily for you Acunetix compiles an annual web application vulnerability report which is a fairly hefty piece of analysis on data gathered from the previous year. This is compiled from […]
Archives for February 2019
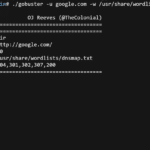
GoBuster – Directory/File & DNS Busting Tool in Go
GoBuster is a Go-based tool used to brute-force URIs (directories and files) in web sites and DNS subdomains (with wildcard support) – essentially a directory/file & DNS busting tool. The author built YET ANOTHER directory and DNS brute forcing tool because he wanted.. … something that didn’t have a fat Java GUI (console FTW). … […]
BDFProxy – Patch Binaries via MiTM – BackdoorFactory + mitmproxy
BDFProxy allows you to patch binaries via MiTM with The Backdoor Factory combined with mitmproxy enabling on the fly patching of binary downloads (software updates for example) from vendors that don’t validate data integrity. The Backdoor Factory allows you to patch binaries with shell-code so combining that with mitmproxy, which is a Python proxy-server that […]