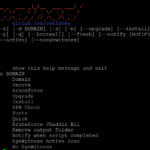
Domained is a multi tool subdomain enumeration tool that uses several subdomain enumeration tools and wordlists to create a unique list of subdomains that are passed to EyeWitness for reporting. This produces categorized screenshots, server response headers and signature based default credential checking. It is written in Python heavily leveraging Recon-ng. Domains Subdomain Enumeration Tools […]
Footer
Most Viewed Posts
- Brutus Password Cracker – Download brutus-aet2.zip AET2 (2,185,029)
- Darknet – Hacking Tools, Hacker News & Cyber Security (2,172,423)
- Top 15 Security Utilities & Download Hacking Tools (2,095,495)
- 10 Best Security Live CD Distros (Pen-Test, Forensics & Recovery) (1,198,763)
- Password List Download Best Word List – Most Common Passwords (932,058)
- wwwhack 1.9 – wwwhack19.zip Web Hacking Software Free Download (774,643)
- Hack Tools/Exploits (672,660)
- Wep0ff – Wireless WEP Key Cracker Tool (528,983)
Search
Recent Posts
- Best EDR Of The Market (BEOTM) – Endpoint Detection and Response Testing Tool January 5, 2024
- AgentSmith HIDS – Host Based Intrusion Detection August 31, 2023
- padre – Padding Oracle Attack Exploiter Tool May 28, 2023
- Privacy Implications of Web 3.0 and Darknets March 31, 2023
- DataSurgeon – Extract Sensitive Information (PII) From Logs March 21, 2023
- Pwnagotchi – Maximize Crackable WPA Key Material For Bettercap February 12, 2023
Tags
apple
botnets
computer-security
darknet
Database Hacking
ddos
dos
exploits
fuzzing
google
hacking-networks
hacking-websites
hacking-windows
hacking tool
Information-Security
information gathering
Legal Issues
malware
microsoft
network-security
Network Hacking
Password Cracking
pen-testing
penetration-testing
Phishing
Privacy
Python
scammers
Security
Security Software
spam
spammers
sql-injection
trojan
trojans
virus
viruses
vulnerabilities
web-application-security
web-security
windows
windows-security
Windows Hacking
worms
XSS