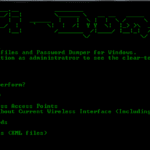
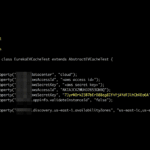
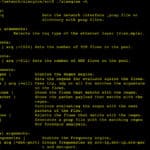
WiFi-Dumper is an open-source Python-based tool to dump WiFi profiles and cleartext passwords of the connected access points on a Windows machine. This tool will help you in a Wifi penetration testing and could also be useful when performing red team assessments or internal infrastructure engagements. Each option in the tool generates the “.txt” file […]
Archives for 2019
truffleHog – Search Git for High Entropy Strings with Commit History
truffleHog is a Python-based tool to search Git for high entropy strings, digging deep into commit history and branches. This is effective at finding secrets accidentally committed. truffleHog previously functioned by running entropy checks on git diffs. This functionality still exists, but high signal regex checks have been added, and the ability to surpress entropy […]
AIEngine – AI-driven Network Intrusion Detection System
AIEngine is a next-generation interactive/programmable Python/Ruby/Java/Lua and Go AI-driven Network Intrusion Detection System engine with capabilities of learning without any human intervention, DNS domain classification, Spam detection, network collector, network forensics and many others. AIEngine also helps network/security professionals to identify traffic and develop signatures for use them on NIDS, Firewalls, Traffic classifiers and so […]
Sooty – SOC Analyst All-In-One CLI Tool
Sooty is a tool developed with the task of aiding a SOC analyst to automate parts of their workflow and speed up their process. The main goal of Sooty is to perform as much of the routine checks as possible which allows the analyst more time to spend on deeper analysis. Features of Sooty SOC […]
UBoat – Proof Of Concept PoC HTTP Botnet Project
UBoat is a PoC HTTP Botnet designed to replicate a full weaponised commercial botnet like the famous large scale infectors Festi, Grum, Zeus and SpyEye. Reviews of popular botnets have shown HTTP-based botnets have a set of attributes that make it difficult for them to be detected. On the other hand, the number of studies […]