So after the massive DDoS attack trend in 2016 it seems like 2018 is going to the year of the Memcached DDoS amplification attack with so many insecure Memcached servers available on the public Internet.
Unfortunately, it looks like a problem that won’t easily go away as there are so many publically exposed, poorly configured Memcached servers online (estimated to be over 100,000).
Honestly, Github handled the 1.3Tbps attack like a champ with only 10 minutes downtime although they did deflect it by moving traffic to Akamai.
Last week, the code repository GitHub was taken off air in a 1.3Tbps denial of service attack. We predicted then that there would be more such attacks and it seems we were right.
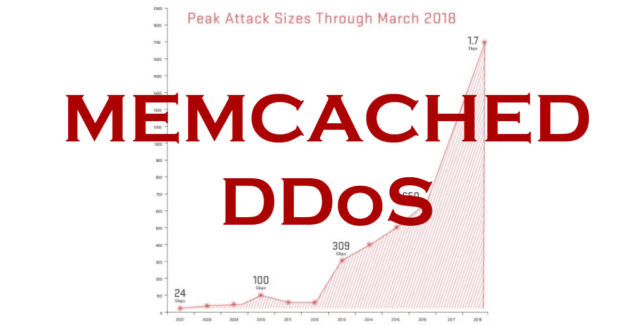
Arbor Networks is now reporting that a US service provider suffered a 1.7Tbps attack earlier this month. In this case, there were no outages as the provider had taken adequate safeguards, but it’s clear that the memcached attack is going to be a feature network managers are going to have to take seriously in the future.
The attacks use shoddily secured memcached database servers to amplify attacks against a target. The assailant spoofs the UDP address of its victim and pings a small data packet at a memcached server that doesn’t have an authenticated traffic requirement in place. The server responds by firing back as much as 50,000 times the data it received.
Then less than a week later, there appears to have been another record-breaking Memcached DDoS attack this time clocking in at 1.7Tbps, although we don’t currently know who it was aimed at.
The amplification is fairly significant as well with the Memcached servers sending up to 50,000 times the data recieved to the unwitting victim, I imagine they are sending some kind of command to retrieve all key value pairs available on the server to the spoofed IP – which could be a significant amount of traffic.
With multiple data packets sent out a second, the memcached server unwittingly amplifies the deluge of data that can be sent against the target. Without proper filtering and network management, the tsunami of data can be enough to knock some providers offline.
There are some simple mitigation techniques, notably blocking off UDP traffic from Port 11211, which is the default avenue for traffic from memcached servers. In addition, the operators of memcached servers need to lock down their systems to avoid taking part in such denial of service attacks.
“While the internet community is coming together to shut down access to the many open memcached servers out there, the sheer number of servers running memcached openly will make this a lasting vulnerability that attackers will exploit,” said Carlos Morales, VP of sales, engineering and operations at Arbor Networks.
“It is critically important for companies to take the necessary steps to protect themselves.”
Memcached servers, like any other part of a well-built infrastructure, should be only listening on the LAN IP address, not the public IP (like any database), but like the whole MongoDB Ransack fiasco, it’s much easier to listen on * and Memcached typically is used without any type of authentication.
I suspect we will see many more of these Memcached DDoS attacks through-out 2018, and probably more targeted. I’m not sure why people love to target Github – perhaps because it’s just so resilient it’s a good test target to see how effective you are.
Source: The Register
