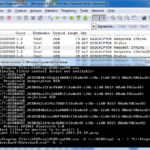
USBPcap is an open-source USB Packet Capture tool for Windows that can be used together with Wireshark in order to analyse USB traffic without using a Virtual Machine. Currently, the live capture can be done on “standard input” capture basis: you write a magic command in cmd.exe and you get the Wireshark to capture raw […]
Archives for January 2018
OWASP ZSC – Obfuscated Code Generator Tool
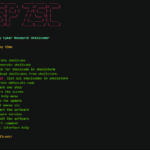
OWASP ZSC is an open source obfuscated code generator tool in Python which lets you generate customized shellcodes and convert scripts to an obfuscated script. Shellcodes are small codes in Assembly language which could be used as the payload in software exploitation. Other usages are in malware, bypassing antivirus software, obfuscating code for protection and […]
A Look Back At 2017 – Tools & News Highlights
So here we are in 2018, taking a look back at 2017, quite a year it was. We somehow forgot to do this last year so just have the 2015 summary and the 2014 summary but no 2016 edition. 2017 News Stories All kinds of things happened in 2017 starting with some pretty comical shit […]
Spectre & Meltdown Checker – Vulnerability Mitigation Tool For Linux
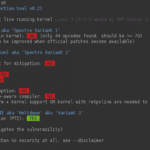
Spectre & Meltdown Checker is a simple shell script to tell if your Linux installation is vulnerable against the 3 “speculative execution” CVEs that were made public early 2018. Without options, it’ll inspect you currently running kernel. You can also specify a kernel image on the command line, if you’d like to inspect a kernel […]
Hijacker – Reaver For Android Wifi Hacker App
Hijacker is a native GUI which provides Reaver for Android along with Aircrack-ng, Airodump-ng and MDK3 making it a powerful Wifi hacker app. It offers a simple and easy UI to use these tools without typing commands in a console and copy & pasting MAC addresses. Features of Hijacker Reaver For Android Wifi Hacker App […]