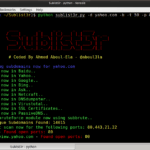
Sublist3r is a Python-based tool designed to enumerate subdomains of websites using OSINT. It helps penetration testers and bug hunters collect and gather subdomains for the domain they are targeting. It also integrates with subbrute for subdomain brute-forcing with word lists. Features of Sublist3r Subdomain Enumeration Tool It enumerates subdomains using many search engines such […]
Archives for December 2017
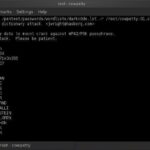
coWPAtty Download – Audit Pre-shared WPA Keys
coWPAtty is a C-based tool for running a brute-force dictionary attack against WPA-PSK and audit pre-shared WPA keys. If you are auditing WPA-PSK networks, you can use this tool to identify weak passphrases that were used to generate the PMK. Supply a libpcap capture file that includes the 4-way handshake, a dictionary file of passphrases […]
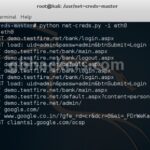
net-creds – Sniff Passwords From Interface or PCAP File
net-creds is a Python-based tool for sniffing plaintext passwords and hashes from a network interface or PCAP file – it doesn’t rely on port numbers for service identification and can concatenate fragmented packets. Features of net-creds for Sniffing Passwords It can sniff the following directly from a network interface or from a PCAP file: URLs […]
DAST vs SAST – Dynamic Application Security Testing vs Static
In security testing, much like most things technical there are two very contrary methods, Dynamic Application Security Testing or DAST and Static Application Security Testing or SAST. Dynamic testing relying on a black-box external approach, attacking the application in its running state as a regular malicious attacker would. Static testing is more white-box looking at […]
Cr3dOv3r – Credential Reuse Attack Tool
Cr3dOv3r is a fairly simple Python-based set of functions that carry out the prelimary work as a credential reuse attack tool. You just give the tool your target email address then it does two fairly straightforward (but useful) jobs: Search for public leaks for the email and if it any, it returns with all available […]