WAFNinja is a Python-based Web Application Firewall Attack Tool designed to help penetration testers execute WAF bypass by automating the steps necessary to bypass input validation.
The tool was created with the objective to be easily extendible, simple to use and usable in a team environment.
What can WAFNinja Web Application Firewall Attack Tool Do?
Many payloads and fuzzing strings, which are stored in a local database file come shipped with the tool.
WAFNinja supports:
- HTTP connections
- GET requests
- POST requests
- Using Cookies (for pages behind auth)
- Intercepting proxy
Using WAFNinja for WAF Bypass
|
1 |
wafninja.py [-h] [-v] {fuzz, bypass, insert-fuzz, insert-bypass, set-db} ... |
Examples of Web Application Firewall Attacks
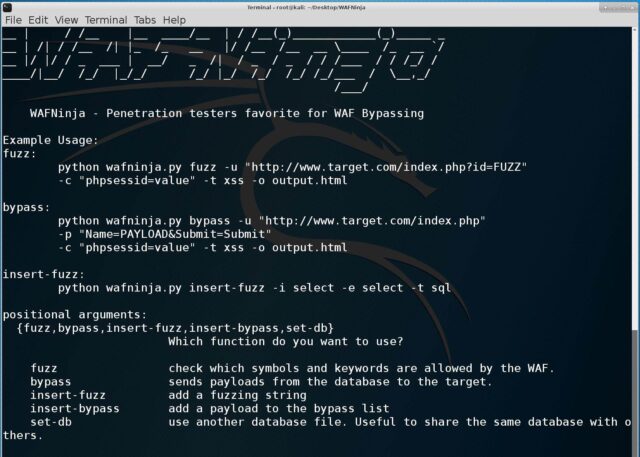
Fuzz:
|
1 |
python wafninja.py fuzz -u "http://www.target.com/index.php?id=FUZZ" -c "phpsessid=value" -t xss -o output.html |
Bypass:
|
1 |
python wafninja.py bypass -u "http://www.target.com/index.php" -p "Name=PAYLOAD&Submit=Submit" -c "phpsessid=value" -t xss -o output.html |
Insert-fuzz:
|
1 |
python wafninja.py insert-fuzz -i select -e select -t sql |
You can also check out:
– WAFW00F – Fingerprint & Identify Web Application Firewall (WAF) Products
You can download WAFNinja here:
Or read more here.

madtester says
This does not work against F5 ASM despite the claims in the review article here:
https://waf.ninja/review-wafninja/
Darknet says
Worked on an earlier version maybe?
mishka says
The tool wasn’t changed for a year and according to article it has only one XSS payload related to F5 ASM. Probably, it was just mitigated with additional rules and guess the same applies to the rest of vendor-specific payloads.