A2SV is a Python-based SSL Vulnerability focused tool that allows for auto-scanning and detection of the common and well-known SSL Vulnerabilities.
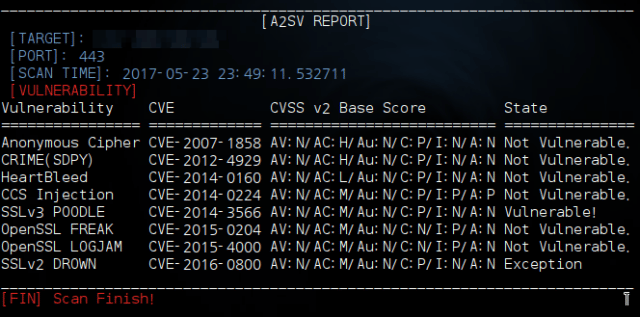
SSL Vulnerabilities Detected by A2SV
- [CVE-2007-1858] Anonymous Cipher
- [CVE-2012-4929] CRIME(SPDY)
- [CVE-2014-0160] CCS Injection
- [CVE-2014-0224] HeartBleed
- [CVE-2014-3566] SSLv3 POODLE
- [CVE-2015-0204] FREAK Attack
- [CVE-2015-4000] LOGJAM Attack
- [CVE-2016-0800] SSLv2 DROWN
Planned for future:
- [PLAN] SSL ACCF
- [PLAN] SSL Information Analysis
Installation & Requirements for A2SV
A. Download(clone) & Unpack A2SV
|
1 2 |
git clone https://github.com/hahwul/a2sv.git cd a2sv |
B. Install Python Package / OpenSSL
|
1 2 3 |
pip install argparse pip install netaddr apt-get install openssl |
C. Run A2SV
|
1 |
python a2sv.py -h |
How to use A2SV Auto Scanning SSL Vulnerability Tool
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 |
usage: a2sv [-h] [-t TARGET] [-tf TARGETFILE] [-p PORT] [-m MODULE] [-d DISPLAY] [-u] [-v] optional arguments: -h, --help show this help message and exit -t TARGET, --target TARGET Target URL and IP Address > e.g -t 127.0.0.1 -tf TARGETFILE, --targetfile TARGETFILE Target file(list) URL and IP Address > e.g -tf ./target.list -p PORT, --port PORT Custom Port / Default: 443 > e.g -p 8080 -m MODULE, --module MODULE Check SSL Vuln with one module [anonymous]: Anonymous Cipher [crime]: Crime(SPDY) [heart]: HeartBleed [ccs]: CCS Injection [poodle]: SSLv3 POODLE [freak]: OpenSSL FREAK [logjam]: OpenSSL LOGJAM [drown]: SSLv2 DROWN -d DISPLAY, --display DISPLAY Display output [Y,y] Show output [N,n] Hide output -o OUT, --out OUT Result write to file > e.g -o /home/yourdir/result.txt -u, --update Update A2SV (GIT) -v, --version Show Version |
You can download A2SV SSL Vulnerability Scanner here:
Or read more here.
