nbtscan is a command-line NetBIOS scanner for Windows that is SUPER fast, it scans for open NetBIOS nameservers on a local or remote TCP/IP network, and this is the first step in the finding of open shares.
It is based on the functionality of the standard Windows tool nbtstat, but it operates on a range of addresses instead of just one.
What is nbtscan?
NETBIOS is commonly known as the Windows “Network Neighborhood” protocol, and (among other things), it provides a name service that listens on UDP port 137. When it receives a query on this port, it responds with a list of all services it offers. Windows ships with a standard tool nbtstat which queries a single IP address when given the -A parameter. When running against a machine on the local network (a development box), it shows:
|
1 2 3 4 5 6 7 8 9 10 11 12 |
C:\> nbtstat -A 192.168.1.99 NetBIOS Remote Machine Name Table Name Type Status --------------------------------------------- XPDEV <00> UNIQUE Registered UNIXWIX <00> GROUP Registered XPDEV <03> UNIQUE Registered XPDEV <20> UNIQUE Registered UNIXWIX <1E> GROUP Registered MAC Address = 00-50-04-6D-50-37 |
The numeric code (in hexadecimal) and the type serve to identify the service being offered, and (for instance) a UNIQUE code of <20> indicates that the machine is running the file-sharing service. Unfortunately, nbtstat only reports the codes, and it requires looking up the meanings elsewhere. The References section at the end of this document lists some resources to learn what all the codes mean.
Machines participating in NetBIOS listen on UDP port 137 for these queries and respond accordingly. Simple configurations might only have a few resource records (as above), but an NT server supporting a large enterprise could easily have more than a dozen. Though it’s sometimes useful to examine the full set of resource records for a given machine, in practice it’s more useful to summarize them into the key “interesting” services.
Our tool has taken this approach. Not only does it scan ranges of addresses — instead of just one machine — but it can fully decode most of the resource record types and can summarize the interesting data on a one-line display.
On our network, we have quite a few machines, but it appears that only three respond to our queries:
|
1 2 3 4 5 |
C:\> nbtscan 192.168.1.0/24 192.168.1.3 MTNDEW\WINDEV SHARING DC 192.168.1.5 MTNDEW\TESTING 192.168.1.9 MTNDEW\WIZ SHARING U=STEVE 192.168.1.99 MTNDEW\XPDEV SHARING |
Using nbtscan NetBIOS Scanner
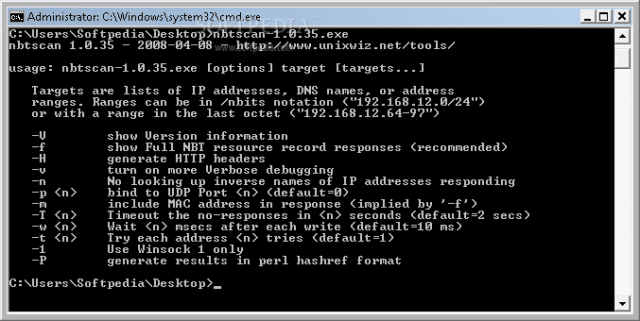
When nbtscan is run without command-line arguments, it reports a short “help” listing that summarizes the options available, which are expanded on here.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
--version / -V -This simply shows the current version information, and I try to keep it updated on each rebuild. Version history is below. -f - This shows the full NBT resource record responses for each machine scanned, not just the one-line summary. This is recommended when studying one single machine, but it's much less useful when scanning a larger range. -O outfile - Send results to outfile rather than to the standard output. -H - Generate an HTTP header. During penetration testing, sometimes we are able to install the nbtscan.exe program on a remote IIS web server and run it with the "Unicode" exploit, but since the output is "regular" text, the output gets confused by the web server that thinks it's a broken CGI script. The -H option addes a simple Content-type: text/plain header with a blank line that makes the output show up correctly. -P - Generate Perl hashref output, which can be loaded into an existing program for easier processing. This is much easier than parsing text output. -v - This turns on some more verbose debugging, but this is really only meant for the developer's use and probably won't help an end-user that much. The code considered "verbose" changes from release to release as bugs are tracked down, and we make no effort to make this useful in the general case. -n - In a few reporting modes, the IP address of the remote machine is used as a key to look up the "inverse" name. This is normally helpful, but many nameservers are misconfigured in a way that make this appear to "hang", so -n turns off this inverse name lookup. -p port - This allows specification of a UDP port number to be used as the source in sending a query. Normally the program picks a random ephemeral port number, and this is entirely sufficient in most cases. But some Windows 95 machines send their responses to port 137 no matter where the query came from (we consider this a bug), so using -p 137 will force nbtscan to bind to this port instead of the random one. In addition, some older versions of the ZoneAlarm personal firewall would incorrectly allow NETBIOS queries if the source port is 53 (DNS). But note that you can't bind to a port that already is in use, and on Windows this usually means that port 137 is unavailable to you. -m - Include the MAC (aka "Ethernet") addresses in the response, which is already implied by the -f option. -T secs - When scanning a large range of addresses, it's not always clear when we are "finished". If we send out (say) five queries, we're clearly done when we get five responses, but if any machine does not respond, we have to rely on timeouts. The -T option controls how long we'll wait for any response, and the default is 2 seconds. -w msecs - Unless the local network is being scanned, we cannot typically blast many queries lest packets be lost on the way. We normally pause for a short time after each network write operation to allow things to clear out before sending another, and this allows the "tuning" of that time. It is specified in milliseconds, and the default is 10 milliseconds. -t tries - Try each address up to tries times, which is useful when dealing with a remote network that is (somehow) dropping packets. Once a given machine has responded, it won't be queried again. Default = 1. -n - Don't look up inverse DNS names in the full listing (show IP addresses). -1 - Force the use of Winsock version 1 (Windows only) rather than the default which is usually version 2. |
If you want something to screw with a tool like nbtscan you can check out something like Fake NetBIOS Tool – Simulate Windows Hosts.
Download nbtscan
Windows – The Win32 version of the tool, which works well on Windows 9x, NT and 2000, is available below as nbtscan.exe. It’s written in portable C and is less than 40 kbytes, requires no special libraries or DLLs, and is run in a MS-DOS command window.
Linux – The code works fine on Linux, and a version built on Red Hat Linux 6.2 is available as well.
You can download nbtscan here:
nbtscan.exe (v1.0.35) – Windows binary (36 kbytes)
nbtscan-1.0.35-redhat-linux – Linux binary (44kbytes)
nbtscan-1.0.31-sco-5.0.6.bin – SCO Open Server 5.0.6
nbtscan-source-1.0.35.tgz (gzip’d tarball)
nbtscan-source-1.0.35.zip (ZIP)
Or read more here.
