It seems to be non-stop lately, this time it’s Deloitte Hacked, which has also revealed all kinds of publically accessible resources that really should be more secure (VPN, RDP & Proxy services).
The irony is that Deloitte positions itself as a global leader in information security and offers consulting services to huge clients all over the planet, now it seems they don’t take their own advice. Honestly this is not all that uncommon, it’s human nature to leave your own stuff last as it doesn’t directly impact revenue or value (until you get hacked).
One of the world’s “big four” accountancy firms has been targeted by a sophisticated hack that compromised the confidential emails and plans of some of its blue-chip clients, the Guardian can reveal.
Deloitte, which is registered in London and has its global headquarters in New York, was the victim of a cybersecurity attack that went unnoticed for months.
One of the largest private firms in the US, which reported a record $37bn (£27.3bn) revenue last year, Deloitte provides auditing, tax consultancy and high-end cybersecurity advice to some of the world’s biggest banks, multinational companies, media enterprises, pharmaceutical firms and government agencies.
The Guardian understands Deloitte Hacked clients across all of these sectors had material in the company email system that was breached. The companies include household names as well as US government departments.
So far, six of Deloitte’s clients have been told their information was “impacted” by the hack. Deloitte’s internal review into the incident is ongoing.
Source: The Guardian
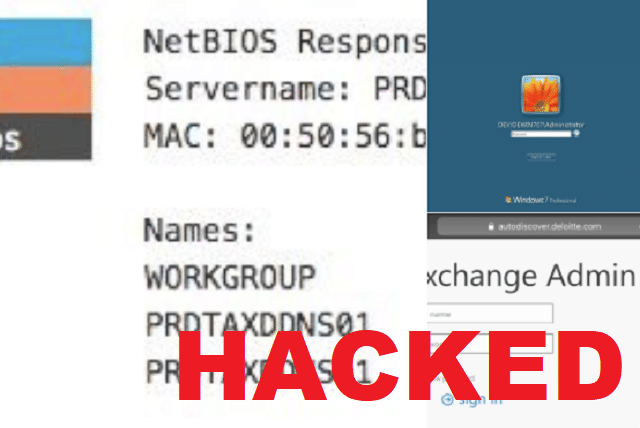
After the Deloitte Hack was revealed a whole bunch of people starting poking around and found a scary amount of fairly private information and resources exposed on the public Internet, easily connected to RDP instances, proxy details posted on an employees Google+ account and VPN servers.
To be fair, Deloitte is a HUGE multi national company and I’d imagine different countries and even cities within countries will have vastly different levels of technological competence and security.
On top of these potential leaks of corporate login details, Deloitte has loads of internal and potentially critical systems unnecessarily facing the public internet with remote-desktop access enabled. All of this gear should be behind a firewall and/or with two-factor authentication as per industry best practices. And likely the best practices Deloitte recommends to its clients, ironically.
“Just in the last day I’ve found 7,000 to 12,000 open hosts for the firm spread across the globe,” security researcher Dan Tentler, founder of Phobos Group, told The Register today. “We’re talking dozens of business units around the planet with dozens of IT departments showing very different aptitude levels. The phrase ‘truly exploitable’ comes to mind.”
For example, he found a Deloitte-owned Windows Server 2012 R2 box in South Africa with RDP wide open, acting as what appears to be an Active Directory server – a crucial apex of a Microsoft-powered network – and with, worryingly, security updates still pending installation. Other cases show IT departments using outdated software, and numerous other security failings.
Honestly, it’s not really surprised – I think if you started profiling and poking around any of the huge companies you’d find a whole lot of things that aren’t supposed to be on the public Internet – even the ones that offer extremely expensive information security services like Deloitte.
It also comes not long after the Equifax Data Breach and the news of Time Warner Hacked.
Source: The Register
