UACme is a compiled, C-based tool which contains a number of methods to defeat Windows User Account Control commonly known as UAC. It abuses the built-in Windows AutoElevate backdoor and contains 41 methods.
The tool requires an Admin account with the Windows UAC set to default settings.
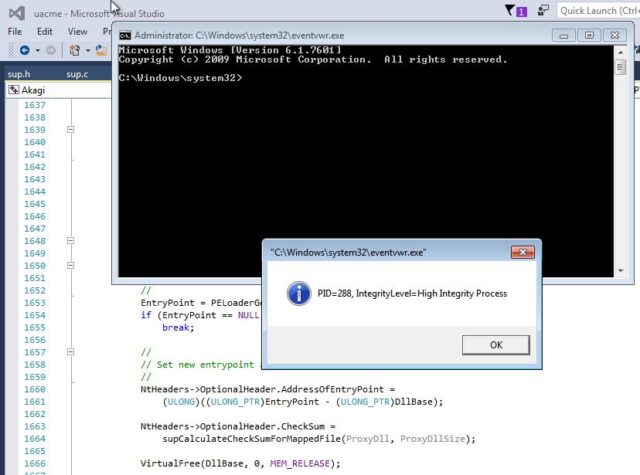
Usage
Run executable from command line: akagi32 [Key] [Param] or akagi64 [Key] [Param].
First param is number of method to use, second is optional command (executable file name including full path) to run. Second param can be empty – in this case program will execute elevated cmd.exe from system32 folder.
Examples:
|
1 2 3 4 |
akagi32.exe 1 akagi64.exe 3 akagi32 1 c:\windows\system32\calc.exe akagi64 3 c:\windows\system32\charmap.exe |
Caveats
- This tool shows ONLY popular UAC bypass method used by malware, and reimplements some of them in a different way improving original concepts. There exists different, not yet known to general public methods, be aware of these
- This tool is not intended for AV tests and not tested to work in an aggressive AV environment, if you still plan to use it with installed bloatware AV soft – you use it at your own risk
- Some AV may flag this tool as HackTool, MSE/WinDefender constantly marks it as malware
- If you run this program on real computer remember to remove all program leftovers after usage, for more info about files it drops to system folders see source code
- Most of the methods are created for x64, with no x86-32 support in mind. The author doesn’t see any sense in supporting 32-bit versions of Windows or wow64. However, with small tweaks, most of them will run under wow64 as well
You can download UACMe here:
Or read more here.
