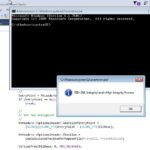
UACme is a compiled, C-based tool which contains a number of methods to defeat Windows User Account Control commonly known as UAC. It abuses the built-in Windows AutoElevate backdoor and contains 41 methods. The tool requires an Admin account with the Windows UAC set to default settings. Usage Run executable from command line: akagi32 [Key] […]
Archives for August 2017
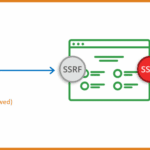
What You Need To Know About Server Side Request Forgery (SSRF)
SSRF or Server Side Request Forgery is an attack vector that has been around for a long time, but do you actually know what it is? Server Side Request Forgery (SSRF) refers to an attack where in an attacker is able to send a crafted request from a vulnerable web application. SSRF is usually used […]
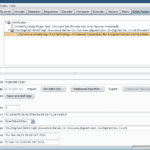
SAML Raider – SAML2 Security Testing Burp Extension
SAML Raider is a Burp Suite extension for SAML2 security testing, it contains two core functionalities – Manipulating SAML Messages and managing X.509 certificates. The extension is divided into two parts, a SAML message editor and a certificate management tool. Features Message Editor Features of the SAML Raider message editor: Sign SAML Messages Sign SAML […]
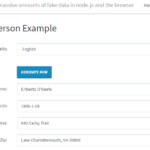
faker.js – Tool To Generate Fake Data For Testing
faker.js is a tool to generate fake data in Node.js and in the browser, it has a lot of different data types to enable you to generate very customised and complete sets of fake or mock data for testing purposes. It also supports multiple languages and locales and can generate a lot of data types […]
Should US Border Cops Need a Warrant To Search Devices?
The answer from me is, OF COURSE, f&ck yes. They can’t search your home, car and anywhere else in the country, they would need a warrant to search devices too. A case by the EFF (Electronic Frontier Foundation) is heading to the Fifth Circuit Court of Appeals in the US to find out what should […]