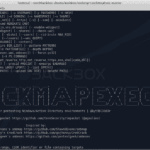
CrackMapExec (a.k.a CME) is a post-exploitation tool that helps automate assessing the security of large Active Directory networks. Built with stealth in mind, CME follows the concept of “Living off the Land”: abusing built-in Active Directory features/protocols to achieve its functionality and allowing it to evade most endpoint protection/IDS/IPS solutions. CME makes heavy use of […]
Archives for July 2017
EvilAbigail – Automated Evil Maid Attack For Linux
EvilAbigail is a Python-based tool that allows you run an automated Evil Maid attack on Linux systems, this is the Initrd encrypted root fs attack. An Evil Maid attack is a type of attack that targets a computer device that has been shut down and left unattended. An Evil Maid attack is characterized by the […]
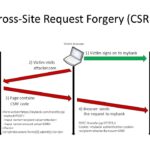
All You Need To Know About Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery is a term you’ve properly heard in the context of web security or web hacking, but do you really know what it means? The OWASP definition is as follows: Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they’re […]
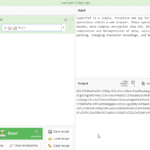
CyberChef – Cyber Swiss Army Knife
CyberChef is a simple, intuitive web app for carrying out all manner of “cyber” operations within a web browser. These operations include simple encoding like XOR or Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character […]
Ghost Phisher – Phishing Attack Tool With GUI
Ghost Phisher is a Wireless and Ethernet security auditing and phishing attack tool written using the Python Programming Language and the Python Qt GUI library, the program is able to emulate access points and deploy. The tool comes with a fake DNS server, fake DHCP server, fake HTTP server and also has an integrated area […]