Prisoners Hack Prison! Sounds exciting right? This time it’s actually pretty entertaining with the prisoners managing to hack a prison network from INSIDE the prison using scavenged PC parts from a rehabilitation class. Some pretty resourceful guys managing to build 2 functional PCs from scrapped parts AND connect to the prison network AND try and […]
Archives for April 2017
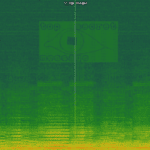
spectrology – Basic Audio Steganography Tool
spectrology is a Python-based audio steganography tool that can convert images to audio files with a corresponding spectrogram encoding, this allows you to hide hidden messages via images inside audio files. Using this tool you can select range of frequencies to be used and all popular image codecs are supported. Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
usage: spectrology.py [-h] [-o OUTPUT] [-b BOTTOM] [-t TOP] [-p PIXELS] [-s SAMPLING] INPUT positional arguments: INPUT Name of the image to be converted. optional arguments: -h, --help show this help message and exit -o OUTPUT, --output OUTPUT Name of the output wav file. Default value: out.wav). -b BOTTOM, --bottom BOTTOM Bottom frequency range. Default value: 200. -t TOP, --top TOP Top frequency range. Default value: 20000. -p PIXELS, --pixels PIXELS Pixels per second. Default value: 30. -s SAMPLING, --sampling SAMPLING Sampling rate. Default value: 44100. |
Example
|
1 |
python spectrology.py test.bmp -b 13000 -t 19000 |
You […]
PowerMemory – Exploit Windows Credentials In Memory
PowerMemory is a PowerShell based tool to exploit Windows credentials present in files and memory, it levers Microsoft signed binaries to hack Windows. The method is totally new. It proves that it can be extremely easy to get credentials or any other information from Windows memory without needing to code in C-type languages. In addition, […]
Microsoft Azure Web Application Firewall (WAF) Launched
Not too long after Amazon launched their cloud protection WAF the Microsoft Azure Web Application Firewall (WAF) has been made generally available in all public Azure DCs. It’s a good move with the majority of websites and services moving into one of the big 3 cloud providers (AWS, Google or Azure) and the vast majority […]
HashData – A Command-line Hash Identifying Tool
HashData is a Ruby-based command-line REPL Hash Identifying Tool with support for a lot of different (most popular) hash types. Installation
|
1 |
$ gem install hashdata |
Usage Command Line When installed, run hashdata and paste in hashes when prompted. Library Example Script:
|
1 2 3 |
require 'hashdata' hash = HashData.new puts(hash.check_type("1111111111111",'DES')) |
The above should output true. The library only matches the start of your second input, this […]