Webbies Toolkit is a pair of tools that enable asynchronous web recon & enumeration including SSL detection, banner grabbing and presence of login forms.
Webbies Features
- Respects scope (including redirects)
- Uses same DNS resolver for enumeration and retrieval by patching aiohttp TCPConnector
- Cached DNS requests by wrapping aiodns
- SSLContext can be modified for specific SSL versions
- Outputs a simple CSV for easy grep-fu of results
- Asynchronous http(s) and dns
- Specialized bingapi search on ip and hostname given bing key
FDB Features
- Fast directory/web application eumeration
- Dir bust numerous hosts simultaneously and save all results in a directory in a CSV file per host
- Task control to limit requests per second
- Multiple progress bars for current status on running FDB’s
- Include word list used, target, extensions, and start and stop times in CSV file
- 404 detection based on response structure and content
Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 |
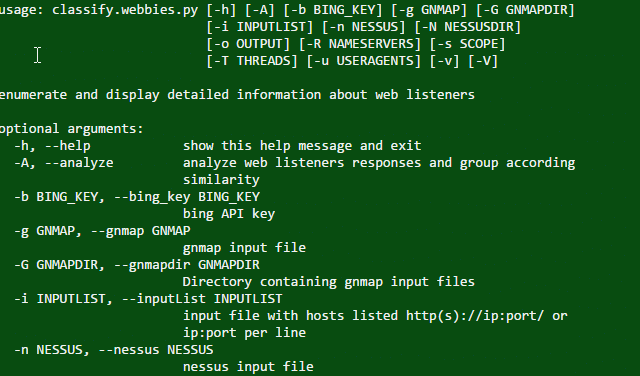
usage: classify.webbies.py [-h] [-A] [-b BING_KEY] [-g GNMAP] [-G GNMAPDIR] [-i INPUTLIST] [-n NESSUS] [-N NESSUSDIR] [-o OUTPUT] [-R NAMESERVERS] [-s SCOPE] [-T THREADS] [-u USERAGENTS] [-v] [-V] enumerate and display detailed information about web listeners optional arguments: -h, --help show this help message and exit -A, --analyze analyze web listeners responses and group according similarity -b BING_KEY, --bing_key BING_KEY bing API key -g GNMAP, --gnmap GNMAP gnmap input file -G GNMAPDIR, --gnmapdir GNMAPDIR Directory containing gnmap input files -i INPUTLIST, --inputList INPUTLIST input file with hosts listed http(s)://ip:port/ or ip:port per line -n NESSUS, --nessus NESSUS nessus input file -N NESSUSDIR, --nessusdir NESSUSDIR Directory containing nessus files -o OUTPUT, --output OUTPUT Output file. Supported types are csv. default is lastrun.csv -R NAMESERVERS, --nameservers NAMESERVERS Specify custom nameservers to resolve IP/hostname. Comma delimited -s SCOPE, --scope SCOPE Scope file with IP Networks in CIDR format -T THREADS, --threads THREADS Set the max number of threads. -u USERAGENTS, --useragents USERAGENTS specifies file of user-agents to randomly use. -v, --verbosity -v for regular output, -vv for debug level -V, --version show program's version number and exit |
You can download Webbies Toolkit here:
Or read more here.
