This is not particularly new news, but the Dark Web paying corporate workers to leak info – especially pertaining to stock prices (earnings reports etc) is setting the mainstream news on fire at the moment.
It’s also funny because people constantly contact us asking questions about the ‘Dark Web’ aka the ‘Dark Net’ which happens to be the name of this site, a name which existed way before Tor did.
Of course the concept of a darknet also way pre-existed Tor as it was a thing way back in the 1970s of designated networks that were isolated from ARPANET.
Staff are taking to the dark web to leak corporate secrets for cash, research reveals.
Hackers from US-based risk management outfit RedOwl and Israeli threat intelligence firm IntSights worked their way past the interview process to access the private darknet property Kick Ass Marketplace, where they found evidence of staff selling internal corporate secrets to hackers. In some cases, staff even collaborated with blackhats to infect their company networks with malware.
The staff at an unnamed bank were also found to be helping hackers maintain a persistent presence on their corporate networks.
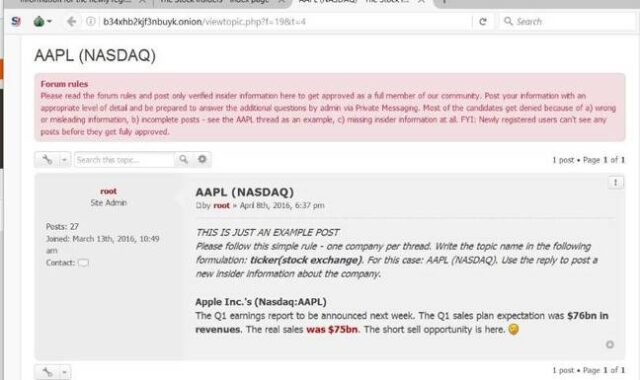
Clients can pay a subscription of up to one bitcoin a month for access to allegedly vetted and accurate insider information which is posted in threads on the site, then cash in on the information they glean.
The site is run in part by an administrator known as “h3x” who in a May interview with DeepDotWeb claimed to be a “self-taught cryptographer, economist, investor, and entrepreneurial businessman”.
h3x has claimed that Kick Ass Marketplace boasts seven administrators, including three hackers and two trading analysts who observe financial markets and vet the integrity of stolen data before posting it to the site.
It is pretty nefarious, though and is giving more ammunition to the naysayers that the dark web is a bad thing and is giving the malicious actors a place to hide.
A story that has been trotted out since the Silk Road bust made the existence of Tor (and what goes on inside the network) pretty mainstream.
Another dark website the trio studied, dubbed The Stock Insiders, recruits retail staff as mules to help cash out stolen credit cards for reliably-resellable goods like Apple iPhones.
The report includes posts where fraudsters seek help from strikers, people willing to walk into stores with stolen credit cards pretending to be legitimate account holders who approach cooperating sales clerks to buy goods.
The trio said insider recruitment is “active and growing” with chatter across public and private forums about the subject doubling from 2015 to 2016.
“The dark web has created a market for employees to easily monetise insider access,” the researchers say.
“The dark web serves as a vehicle insiders use to cash out on their services through insider trading and payment for stolen credit cards.
“Sophisticated threat actors use the dark web to find and engage insiders to help place malware behind an organisation’s perimeter security [and] as a result, any insider with access to the internal network, regardless of technical capability or seniority, presents a risk.”
Insider theft can be disastrous for some organisations. In Australia, theft of sensitive corporate information including designs and customer records can be considered a civil rather than criminal matter, leading to very lengthy and expensive lawsuits.
It’s pretty hard to stop, or even trace such perpetrators if they have any reasonable understanding of OPSEC. Which by the looks of it, they have as the networks have been infiltrated by infosec companies and they haven’t been busted yet.
It doesn’t mean given time they won’t be busted though, so we’ll be watching for news of that.
Source: The Register
