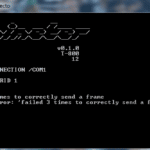
Termineter is a Python Smart Meter Security Testing framework which allows authorised individuals to test Smart Meters for vulnerabilities such as energy consumption fraud, network hijacking, and more. Many of these vulnerabilities have been highlighted by the media and advisories have been sent out by law enforcement agencies. The goal of a public release for […]
Archives for February 2017
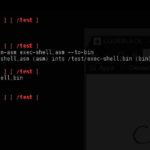
ShellNoob – Shellcode Writing Toolkit
ShellNoob is a Python-based Shellcode writing toolkit which removes the boring and error-prone manual parts from creating your own shellcodes. Do note this is not a shellcode generator or intended to replace Metasploit’s shellcode generator, it’s designed to automate the manual parts of shellcode creation like format conversion, compilation and testing, dealing with syscalls and […]
Visiting The States? Have Your Passwords Ready
There’s been a lot of buzz about this on Twitter, if you’re visiting the states anytime soon you might want to have your social media login credentials handy – as they might be requesting them at the border. I find the whole thing rather contrived though as I use 2FA for everything, so they are […]
crackle – Crack Bluetooth Smart Encryption (BLE)
crackle is a tool to crack Bluetooth Smart Encryption (BLE), it exploits a flaw in the pairing mechanism that leaves all communications vulnerable to decryption by passive eavesdroppers. crackle can guess or very quickly brute force the TK (temporary key) used in the pairing modes supported by most devices (Just Works and 6-digit PIN). With […]
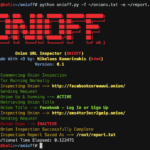
ONIOFF – Onion URL Inspector
ONIOFF is basically an Onion URL inspector, it’s a simple tool – written in pure python – for inspecting Deep Web URLs (or onions). It takes specified onion links and returns their current status along with the site’s title. It’s compatible with Python 2.6 & 2.7. Usage
|
1 |
Usage: python onioff.py {onion} [options] |
To view all available options run:
|
1 |
$ python onioff.py -h |
[…]