Not long after releasing v11 of their scanner, Acunetix has decided to deliver free manual pen-testing tools. Previously these tools were only available to paying Acunetix customers, now anyone can use them to make their manual web application testing easier. Penetration testers can make use of an HTTP Editor to modify or craft HTTP requests […]
Archives for January 2017
ZGrab – Application Layer Scanner For ZMap
ZGrab is a Go-based application layer scanner that operates with ZMap and supports multiple protocols and services including TLS, IMAP, SMTP, POP3 etc. It also stores TLS version and can detect Heartbleed. Building You will need to have a valid $GOPATH set up, for more information about $GOPATH, see https://golang.org/doc/code.html. Once you have a working […]
p0wnedShell – PowerShell Runspace Post Exploitation Toolkit
p0wnedShell is an offensive PowerShell Runspace Post Exploitation host application written in C# that does not rely on powershell.exe but runs PowerShell commands and functions within a PowerShell run space environment (.NET). It has a lot of offensive PowerShell modules and binaries included making the process of Post Exploitation easier. What the author tried was […]
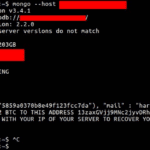
MongoDB Ransack – Over 33,000 Databases Hacked
Ah our favourite database in the news again, being hailed as the MongoDB Ransack a whole bunch of people have turned the insecure MongoDB default configuration into a ransom opportunity. They are deleting/stealing databases and soliciting bitcoin payments to return the data. With multiple actors doing the same stuff though it’s hard to know who […]
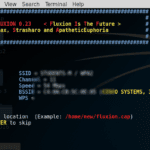
Fluxion – Automated EvilAP Attack Tool
Fluxion is an automated EvilAP attack tool for carrying out MiTM attacks on WPA Wireless networks written in a mix of Bash and Python. Fluxion is heavily based off Linset the Evil Twin Attack Bash Script, with some improvements and bug-fixes. How it Works Scan the networks. Capture a handshake (can’t be used without a […]