Ah our favourite database in the news again, being hailed as the MongoDB Ransack a whole bunch of people have turned the insecure MongoDB default configuration into a ransom opportunity. They are deleting/stealing databases and soliciting bitcoin payments to return the data.
With multiple actors doing the same stuff though it’s hard to know who is legit, and it seems some are just deleting the databases and asking for payment without even having the data.
MongoDB databases are being decimated in soaring ransomware attacks that have seen the number of compromised systems more than double to 27,000 in a day.
Criminals are accessing, copying and deleting data from unpatched or badly-configured databases.
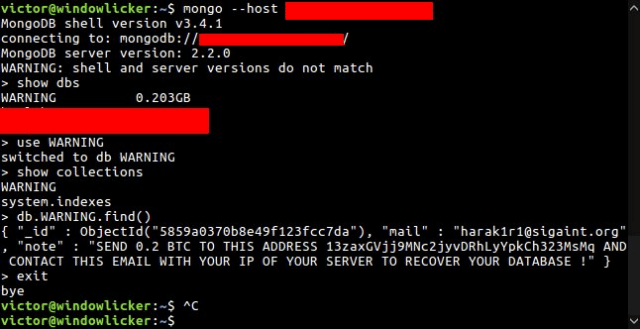
Administrators are being charged ransoms to have data returned. Initial attacks saw ransoms of 0.2 bitcoins (US$184) to attacker harak1r1, of which 22 victims appeared to have paid, up from 16 on Wednesday when the attacks were first reported.
However, some payments could be benign transfers designed to make it appear victims are paying.
Norway-based security researcher and Microsoft developer Niall Merrigan says the attacks have soared from 12,000 earlier today to 27,633, over the course of about 12 hours.
Merrigan and his associates have now logged some 15 distinct attackers. One actor using the email handle kraken0 has compromised 15,482 MongoDB instances, demanding 1 bitcoin (US$921) to have files returned. No one appears to have paid. Merrigan says he is investigating “OSINT and finding different IOCs as well the actors involved”.
It’s not the first time we’ve talked about this too, back when BeautifulPeople.com was hacked it was due to MongoDB and it’s great defaults (listening on all interfaces, including public Internet-facing IP addresses) and not forcing any kind of authentication by default.
Yah you can say it’s the users’ problem, the features are there – but how hard is it to have secure defaults? Newer versions have fixed this, from what I know – but still, the mess caused by their dubious decisions is pretty widespread.
All told, a whopping 99,000 MongoDB installations are exposed, Gevers says.
MongoDB security is a known problem: up until recently, the software’s default configuration is insecure. Shodan founder John Matherly warned in 2015 that some 30,000 exposed MongoDB instances were open to the internet without access controls.
In the Antipodes, the Australian Communications and Media Authority has been reporting exposed MongoDB installations since July 2015 using intelligence provided by the ShadowServer nonprofit.
Bruce Matthews, manager of the agency’s cyber security and unsolicited communications enforcement section, told Vulture South it has insight into IP ranges covering 90 percent of Australia.
He says the number of exposed MongoDB databases in Australia appears to remain steady.
“We report open and vulnerable services to AISI who can pass on the information to the operator of the service,” Matthews says. “It is important that the information is passed on.”
It’s not terribly hard to fix either, assuming it installed on the same server as the web host (if not why else would a DB have a Public IP?), just bind it to localhost and enable authentication for all databases.
The problem now is all these ‘agile’ tools, DevOps deploying gists on Github and automated server creation means developers with no clue about security are rolling up database servers and just using them. I blame the MEAN stack.
Source: The Register

R.zDB2-er says
Go MainFrame, zDB2 Baby!