dns2proxy is an offensive DNS server that offers various features for post-exploitation once you’ve changed the DNS server of a victim.
It’s very frequently used in combination with sslstrip.
Features
- Traditional DNS Spoofing
- Implements DNS Spoofing via Forwarding
- Detects and corrects changes for sslstrip to work
Usage
Using the spoof.cfg config file with the format:
|
1 |
hostname ip.ip.ip.ip |
|
1 2 3 4 5 6 7 8 9 10 11 12 |
root@kali:~/dns2proxy# echo "www.s21sec.com 1.1.1.1" > spoof.cfg // launch in another terminal dns2proxy.py root@kali:~/dns2proxy# nslookup www.s21sec.com 127.0.0.1 Server: 127.0.0.1 Address: 127.0.0.1#53 Name: www.s21sec.com Address: 1.1.1.1 Name: www.s21sec.com Address: 88.84.64.30 |
Or you can use domains.cfg file to spoof all hosts of a domain (wildcard):
|
1 2 3 4 5 6 7 8 9 |
root@kali:~/demoBH/dns2proxy# cat dominios.cfg .domain.com 192.168.1.1 root@kali:~/demoBH/dns2proxy# nslookup aaaa.domain.com 127.0.0.1 Server: 127.0.0.1 Address: 127.0.0.1#53 Name: aaaa.domain.com Address: 192.168.1.1 |
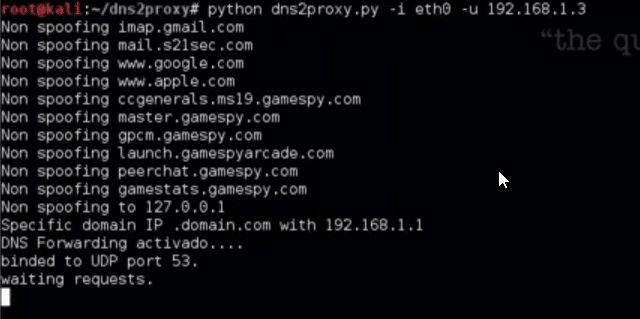
Hostnames at nospoof.cfg will not be spoofed.
Config Files
domains.cfg – resolve all hosts/subdomains for the listed domains with the given IP.
|
1 |
.facebook.com 1.2.3.4 .fbi.gov 1.2.3.4 |
spoof.cfg – Spoof a single host with a given IP.
|
1 |
www.nsa.gov 127.0.0.1 |
nospoof.cfg – Send always a legit response when responding for these hosts.
|
1 |
mail.google.com |
nospoofto.cfg – Don’t send fake responses to the IPs listed there.
|
1 |
127.0.0.1 4.5.6.8 |
victims.cfg – If not empty, only send fake responses to these IP addresses.
|
1 |
23.66.163.36 195.12.226.131 |
resolv.conf DNS server to forward legitimate queries to.
|
1 |
nameserver 8.8.8.8 |
You can download dns2proxy here:
Or read more here.
