The ETOpen Ruleset is an excellent anti-malware IDS/IPS ruleset that enables users with cost constraints to significantly enhance their existing network-based malware detection. The ETOpen Ruleset is not a full coverage ruleset, and may not be sufficient for many regulated environments and should not be used as a standalone ruleset. The ET Open ruleset is […]
Archives for August 2016
Bearded – Security Automation Platform
Bearded is an open source Security Automation platform. The platform allows Development, QA, and Security team members to perform automated web security scans with a set of tools, and re-execute those scans as needed. All tools can be executed in the cloud in docker containers. Bearded has a default web interface which integrates all core […]
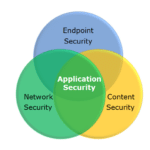
An Introduction To Web Application Security Systems
In the world of web application security systems, there exists a myriad of systems to protect public-facing services in any number of ways. They come packed with all the elements necessary to play an action-packed round of buzzword bingo, but they often overlap in some ways that may make them sometimes seem similar. After the second […]
IGHASHGPU – GPU Based Hash Cracking – SHA1, MD5 & MD4
IGHASHGPU is an efficient and comprehensive command line GPU based hash cracking program that enables you to retrieve SHA1, MD5 and MD4 hashes by utilising ATI and nVidia GPUs. It even works with salted hashes making it useful for MS-SQL, Oracle 11g, NTLM passwords and others than use salts. IGHASHGPU is meant to function with […]
PowerOPS – PowerShell Runspace Portable Post Exploitation Tool
PowerShell Runspace Portable Post Exploitation Tool aimed at making Penetration Testing with PowerShell “easier”. PowerOPS is an application written in C# that does not rely on powershell.exe but runs PowerShell commands and functions within a powershell runspace environment (.NET). It intends to include multiple offensive PowerShell modules to make the process of Post Exploitation easier. […]