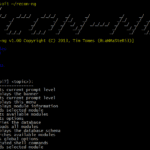
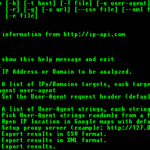
Recon-ng is a full-featured Web Reconnaissance Framework written in Python. Complete with independent modules, database interaction, interactive help, and command completion – Recon-ng provides a powerful environment in which open source web-based reconnaissance can be conducted quickly and thoroughly. Recon-ng has a look and feel and even command flow similar to the Metasploit Framework, reducing […]
Archives for April 2016
IPGeoLocation – Retrieve IP Geolocation Information
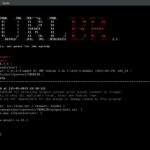
IPGeoLocation is a Python based tool designed to retrieve IP geolocation information from the ip-api service, useful for building into your security tools. Do be aware that as this tool is leveraging a 3rd party API, you will be limited to 150 requests a minute. Whilst that is quite a lot, just be wary of […]
BADLOCK – Are ‘Branded’ Exploits Going Too Far?
So there’s been hype about this big exploit coming, for over a month, before anything was released. It had a name, a website and a logo – and it was called Badlock. And now it’s out, and it’s more like Sadlock – really a local network DoS against DCE/RPC services on Windows and Linux with […]
INURLBR – Advanced Search Engine Tool
INURLBR is a PHP based advanced search engine tool for security professionals, it supports 24 search engines and 6 deep web or special options. Very useful for the information gathering phase of a penetration test or vulnerability assessment. This tool functions in many ways enabling you to harness the power of what’s already indexed by […]
DNSRecon – DNS Enumeration Script
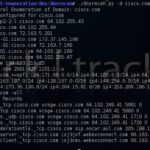
DNSRecon is a Python based DNS enumeration script designed to help you audit your DNS security and configuration as part of information gathering stage of a pen-test. DNS reconnaissance is an important step when mapping out domain resources, sub-domains, e-mail servers and so on and can often lead to you finding an old DNS entry […]