So there’s been a fair bit of noise this past week about the Mac OS X Ransomware, the first of its’ kind called KeRanger. It also happens to be the first popular Mac malware of any form for some time.
It’s also a lesson to all the Apple fanbois that their OS is not impervious and this was bundled with legit software (Transmission) and bypassed the Gatekeeper protection as it was signed with a legit cert.
It turns out, basically it’s just the Linux Encoder Trojan (the first Linux ransomware trojan) re-purposed for Macs, as well OS X is a *nix variant based on OpenBSD with a fancy window manager.
The world’s first fully functional OS X ransomware, KeRanger, is really a Mac version of the Linux Encoder Trojan, according to new research from Romanian security software firm Bitdefender.
The infected OS X torrent update carrying KeRanger looks virtually identical to version 4 of the Linux Encoder Trojan that has already infected thousands of Linux servers this year.
KeRanger spread via an infected version of an otherwise legitimate open source BitTorrent application, Transmission. The tainted version (2.90) was available for download between March 4 and March 5, 2016 and came signed with a legitimate developer certificate.
Apple’s OS X ships with a security feature called Gatekeeper, allowing users to restrict which sources they can install applications from in order to minimize the likelihood of deploying a malicious app. The default setting allows users to install applications from the Mac App Store or applications that are digitally signed by a developer.
By using a developer certificate to sign their wares, the crooks behind KeRanger were able to circumvent Apple’s GateKeeper control. Apple has since revoked the misused certificate, which was issued to a Turkish firm, so the immediate panic is over.
However, similar attacks along the same lines might easily re-appear, so merely disallowing unsigned software from running on Macs is no defense.
It’s a pretty nasty form of cyber-bullying, and well as we wrote before, if you do get hit there’s not a lot you can do. Even the FBI Recommends Crypto Ransomware Victims Just Pay.
The developer cert used to sign the dodgy version of Tranmission has been revoked, but it just goes to show the system is not flawless and this could easily happen again.
KeRanger isn’t the first Mac malware with the capability to circumvent Gatekeeper. For example, three years ago the same trick was used in a trojan (KitM.A) found on computers belonging to Angolan civil rights activists, Bitdefender reports.
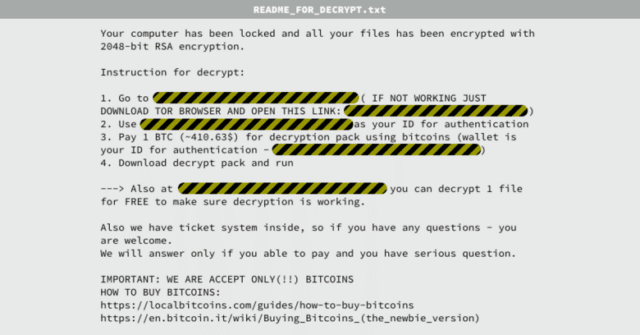
“Once the infected installer is executed, the Trojan connects to the command and control centers via TOR and retrieves an encryption key,” explained Catalin Cosoi, chief security strategist at Bitdefender.
“After encryption finishes, the KeRanger ransomware creates a file called README_FOR_DECRYPT.txt, which holds the information on how the victim should pay the ransom. The encryption functions are identical to those deployed by the Linux Encoder Trojan and have the same names.”
Six months ago, only Windows and Android smartphone users needed to worry about ransomware, but that has changed more recently so that Linux server admins and even Mac users need to be wary of potential attack. Windows remains the target of the greatest number of different ransomware strains and the main locus of the problem, as it is for other types of malware.
The developers behind the Linux Encoder malware have either expanded to OS X or have licensed their code to a cybercrime group specializing in OS X attacks, according to Bitdefender.
I’m pretty sure no one reading this site will get caught out by this kind of thing, but if you did well that mistake is gonna cost you over $400USD.
Be wary, and do inform your Apple loving friends and family members that the bad guys feel like it’s worth targeting them now, the free-love, no anti-virus party is over.
Source: The Register
