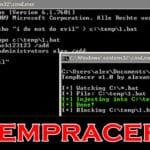
TempRacer is a Windows Privilege Escalation Tool written in C# designed to automate the process of injecting user creation commands into batch files with administrator level privileges. The code itself is not using that many resources because it relies on callbacks from the OS. You can keep it running for the the whole day to […]
Archives for March 2016
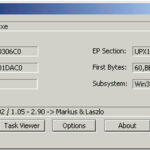
PEiD Download – Detect PE Packers, Cryptors & Compilers
PEiD is an intuitive application that relies on its user-friendly interface to detect PE packers, cryptors and compilers found in executable files – its detection rate is higher than that of other similar tools since the app packs more than 600 different signatures in PE files. What is PEiD? PEiD comes with three different scanning […]
FBI Backed Off Apple In iPhone Cracking Case
So the big furore this week is because the FBI backed off Apple in the whole Apple vs the World privacy case regarding cracking the iPhone Passcode of the phone belonging to the San Bernardino gunman Syed Farook. If you’re not familiar with the case, catch up with it here: FBI–Apple encryption dispute. The latest […]
NAXSI – Open-Source WAF For Nginx
NAXSI is an open-source WAF for Nginx (Web Application Firewall) which by default can block 99% of known patterns involved in website vulnerabilities. NAXSI means Nginx Anti XSS & SQL Injection Technically, it is a third party Nginx module, available as a package for many UNIX-like platforms. This module, by default, reads a small subset […]
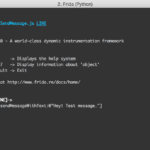
Frida – Dynamic Code Instrumentation Toolkit
Frida is basically Greasemonkey for native apps, or, put in more technical terms, it’s a dynamic code instrumentation toolkit. It lets you inject snippets of JavaScript into native apps on Windows, Mac, Linux, iOS and Android. Frida also provides you with some simple tools built on top of the Frida API. These can be used […]