The LowNoiseHG (LNHG) Massive Web Fingerprinter was conceived in July 2013 after realizing the usefulness of webserver screenshots to pentesters, during an engagement with large external or internal IP address ranges, as a quick means of identification of critical assets, easily-exploitable services, forgotten/outdated servers and basic network architecture knowledge of the target.
The basic operation of mwebfp consists of the processing of an input (targets and TCP ports) that is then used to identify open web server ports with the help of a powerful portscanner (nmap). All ports found open are then analyzed (on HTTP and HTTPS) and all relevant webserver information is recorded, as well as a screenshot of the rendered webpage (as if it is seen from a broswer).
Features
- Input
- Target(s) can be IP address(es), IP address range(s), server name(s), etc.
- Target(s) can be provided directly on the command-line or on a file
- Port Definition
- Default ports are 80 (HTTP) and 443 (HTTPS), but any port can be easily configured at runtime
- Output
- All output files and related support files for the scan are saved on a directory configured at runtime by the user
- Currently, mwebfp exports results on a CSV file (Easily usable on MS Excel) only
- Virtual Hosts
- If requested at runtime, mwebfp will find all virutally hosted domains and webpages for the target server
- Webserver Screenshots
- If requested at runtime, mwebfp will grab screenshots of all found web pages (Graphical UI under Linux is required)
Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 |
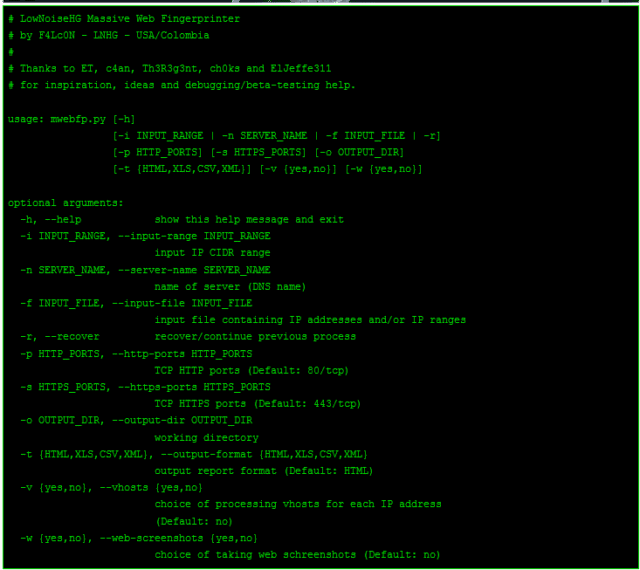
# LowNoiseHG Massive Web Fingerprinter # by F4Lc0N - LNHG - USA/Colombia # # Thanks to ET, c4an, Th3R3g3nt, ch0ks and ElJeffe311 # for inspiration, ideas and debugging/beta-testing help. usage: mwebfp.py [-h] [-i INPUT_RANGE | -n SERVER_NAME | -f INPUT_FILE | -r] [-p HTTP_PORTS] [-s HTTPS_PORTS] [-o OUTPUT_DIR] [-t {HTML,XLS,CSV,XML}] [-v {yes,no}] [-w {yes,no}] optional arguments: -h, --help show this help message and exit -i INPUT_RANGE, --input-range INPUT_RANGE input IP CIDR range -n SERVER_NAME, --server-name SERVER_NAME name of server (DNS name) -f INPUT_FILE, --input-file INPUT_FILE input file containing IP addresses and/or IP ranges -r, --recover recover/continue previous process -p HTTP_PORTS, --http-ports HTTP_PORTS TCP HTTP ports (Default: 80/tcp) -s HTTPS_PORTS, --https-ports HTTPS_PORTS TCP HTTPS ports (Default: 443/tcp) -o OUTPUT_DIR, --output-dir OUTPUT_DIR working directory -t {HTML,XLS,CSV,XML}, --output-format {HTML,XLS,CSV,XML} output report format (Default: HTML) -v {yes,no}, --vhosts {yes,no} choice of processing vhosts for each IP address (Default: no) -w {yes,no}, --web-screenshots {yes,no} choice of taking web schreenshots (Default: no) |
Requirements
In order to run mwebfp “out-of-git”, with all options enabled, you will need:
- Python – Programming language (sudo apt-get instal python)
- nmap – Port Scanner (sudo apt-get install nmap)
- python-nmap – Python module (apt-get install python-nmap)
- requests – Python module (apt-get install python-requests)
- cutycapt – Qt WebKit Capture Utility (You will need the latest version to be able to capture HTTPS pages – do NOT do apt-get !!!)
- A graphical interface (GUI) on the *nix server you are running the script (I assume Linux)
You can download mwebfp here:
Or read more here.
