So this is a big one, and thankfully this PayPal Remote Code Execution Vulnerability was discovered by security researchers and not the bad guys. Although there’s no way for us to know if someone has been using this to siphon data out of PayPal for some time before the whitehats found it.
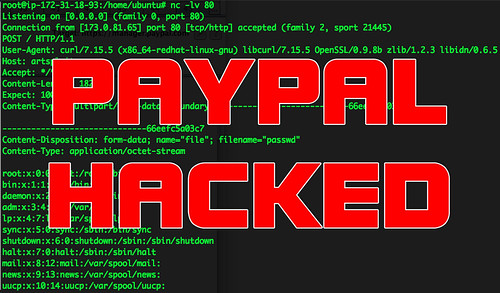
It’s a roundabout bug that turns out serious, and why I tell developers don’t mess with serialised data – it’s ugly. In this case object deserialisation in Java basically allowed for remote command execution on PayPal servers.
Independent security researcher Michael Stepankin has reported a since-patched remote code execution hole in Paypal that could have allowed attackers to hijack production systems.
The critical vulnerability affecting manager.paypal.com revealed overnight was reported 13 December and patched soon after disclosure.
It allowed Stepankin to execute arbitrary shell commands on PayPal web servers through Java object deserialisation opening access to production databases.
“I immediately reported this bug to PayPal security team and it was quickly fixed after that,” Stepankin says
“While security testing of manager.paypal.com, my attention was attracted by unusual post form parameter “oldFormData” that looks like a complex object after base64 decoding.
It was reported responsibly and fixed fairly quickly, PayPal does have quite a good record of reacting in a timely fashion.
You can read the original blog post here: PayPal Remote Code Execution Vulnerability
“After some research I realised that it’s a Java serialised object without any signature handled by the application [which] means that you can send serialised object of any existing class to a server and ‘readObject’ or ‘readResolve’ method of that class will be called.”
Attackers would need to follow the technique disclosed by FoxGlove Security to gain remote code execution.
Stepankin says he used their ‘ysoserial’ payload generation tool in his attack.
PayPal handed out US$5000 for the bug even though it was a duplicate of a report sent in two days prior by researcher Mark Litchfield. Most bug bounty operators do not pay for duplicates making the payment unusual.
Strangely enough it seems to like two researchers found the same bug within days of each other independently. So PayPal paid them both a bounty, which is very rare – and pretty cool IMHO.
You can read about what Mark Litchfield got upto in December here – My $50k Personal Challenge – Results
Pretty good earnings for a months work, although I might imagine he’s had a fair number of those bugs in pocket for a while.
Source: The Register
