So the Fortinet SSH Backdoor, apparently it’s just a management authentication issue. Sorry, what’s that? It looks like a passphrase based admin level access login via SSH to me personally.
Which is scary.
They are adamantly shouting from rooftops that it was not planted by a 3rd party (NSA? Like Juniper..) or any kind of malicious activity.
Enterprise security vendor Fortinet has attempted to explain why its FortiOS firewalls were shipped with hardcoded SSH logins.
It appears Fortinet’s engineers implemented their own method of authentication for logging-into FortiOS-powered devices, and the mechanism ultimately uses a secret passphrase. This code was reverse-engineered by persons unknown, and a Python script to exploit the hole emerged on the Full Disclosure mailing list this week.
Anyone who uses this script against vulnerable firewalls will gain administrator-level command-line access to the equipment. After some outcry on Twitter and beyond, Fortinet responded by saying it has already killed off the dodgy login system.
“This issue was resolved and a patch was made available in July 2014 as part of Fortinet’s commitment to ensuring the quality and integrity of our codebase,” a spokeswoman told El Reg.
“This was not a ‘backdoor’ vulnerability issue but rather a management authentication issue. The issue was identified by our product security team as part of their regular review and testing efforts. After careful analysis and investigation, we were able to verify this issue was not due to any malicious activity by any party, internal or external.”
In a security advisory dated today, Fortinet explained that the issue affects FortiOS versions 4.3.0 to 4.3.16 and 5.0.0 to 5.0.7. This covers FortiOS builds from between November 2012 and July 2014, and it’s certainly possible that some slack IT admins haven’t updated the software since then.
It was actually patched by Fortinet in July 2014, but with edge devices like Firewalls – they don’t often get updated as it usually causes network downtime. So I’d guess there are plenty of firewalls out there very vulnerable to this, which basically gives you full admin access.
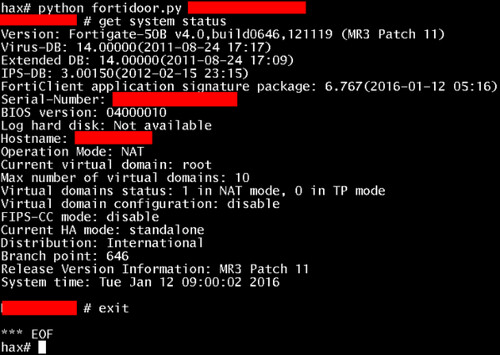
You can find the ‘exploit’ script in Python here: SSH Backdoor for FortiGate OS Version 4.x up to 5.0.7
It’s also possible that even if they did update in a timely fashion, their devices could have been breached before the fix was issued.
The login method is used by FortiManager, a tool for controlling any number of Fortinet devices from a central system.
If you are running older code and can’t upgrade, the firewall maker suggests a couple of workarounds. Managers can disable admin access via SSH and use the web interface instead, or the console browser applet for command-line access. If you really need SSH access, then version 5.x can restrict access to SSH to a minimal set of authorized IP addresses.
Whether you call it a backdoor or a “management authentication issue,” it’s still a pretty major issue for some sysadmins, and they are unlikely to be happy about the news.
One significant part of Fortinet’s statement was the assertion that this didn’t come from an external party. Ever since the Juniper backdooring security vendors have been at pains to avoid any suggestion that they are allowing intelligence agencies access to their products.
In the meantime, if you are using FortiOS then make sure the fimrware is up to date. The news of this hole will have the malicious hacking community aflutter and many are no doubt already scanning for vulnerable targets.
There are some work arounds, what I’d personally like to see though is more transparency about the process and decisions made that led to this code being on production firewalls. How does this even happen?
And how did they only find it during scheduled review and testing? What kind of testing/QA/CI process do they have?
It all sounds rather fishy to me.
Source: The Register
