So FireEye doesn’t have a particularly good reputation in the security community, it’s generally not handled responsible disclosure well and it’s even taken a security firm (ERNW) to court over a vulnerability disclosure. And now there’s another critical remote root zero-day in FireEye appliances – which is scary, as these are high end devices protecting […]
Archives for December 2015
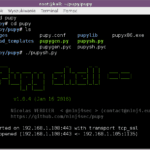
Pupy Download – Open-Source Remote Administration Tool – RAT
Pupy is an open-source remote administration tool (RAT), that is cross-platform and has an embedded Python interpreter, allowing its modules to load Python packages from memory and transparently access remote Python objects. Pupy can communicate using different transports and have a bunch of cool features & modules. On Windows, Pupy uses reflective dll injection and […]
Latest Update Patches 78 CVE-classified Flash Security Vulnerabilities
So as a rule, in 2015 running Adobe Flash is already pretty scary – but the latest patch release covers 78 CVE-classified Flash security vulnerabilities. That’s not scary, that’s terrifying. By now you kinda expect flaws in Flash, it’s just a given. But 78 CVE-classified vulnerabilities in one patch release? That’s just insane, that’s worse […]
SprayWMI – PowerShell Injection Mass Spray Tool
SprayWMI is a method for mass spraying Unicorn PowerShell injection to CIDR notations. It’s an alternative to traditional, ‘noisy’ tools which leave something on the disk like PsExec, smbexec, winexe and so on. These tools have worked really well, however, they are fairly noisy creating a service and touching disk which will trigger modern defense […]
VTech Hack – Over 7 Million Records Leaked (Children & Parents)
And once again, the messy technical flaws of a company are being exposed with the recent VTech hack – it’s really not looking good for them with account passwords ‘secured’ with unsalted md5 hashes and all kinds of private information being leaked includes parents addresses, kids birthdays, genders, secret answers and associated meta-data (IP addresses, […]