The LaZagne project is an open source password recovery tool used to retrieve passwords stored on a local computer. Each software stores its passwords using different techniques (plaintext, APIs, custom algorithms, databases and so on). This tool has been developed for the purpose of finding these passwords for the most commonly-used software. At this moment, it supports 22 Programs on Microsoft Windows and 12 on a Linux/Unix-Like operating systems.
It supports a whole bunch of software including things like CoreFTP, Cyberduck, FileZilla, PuttyCM, WinSCP, Chrome, Firefox, IE, Opera, Jitsi, Pidgin, Outlook, Thunderbird, Tortoise, Wifi passwords and more.
Usage
Retrieve version
|
1 |
cmd: laZagne.exe --version |
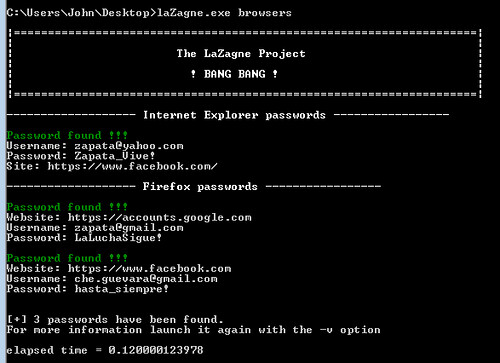
Launch all modules
|
1 |
cmd: laZagne.exe all |
Launch only a specific module
|
1 2 3 |
cmd: laZagne.exe example: laZagne.exe browsers help: laZagne.exe -h |
Launch only a specific software script
|
1 2 3 |
cmd: laZagne.exe example: laZagne.exe browsers -f help: laZagne.exe browsers -h |
Write all passwords found into a file (-w options)
|
1 |
cmd: laZagne.exe all -w |
Use a file for dictionary attacks (used only when it’s necessary: mozilla masterpassword, system hahes, etc.). The file has to be a wordlist in cleartext (no rainbow), it has not been optimized to be fast but could useful for basic passwords.
|
1 |
cmd: laZagne.exe all -path file.txt |
Change verbosity mode (2 different levels)
|
1 |
cmd: laZagne.exe all -vv |
You can download laZagne here:
Windows – laZagne-Windows.zip
Source – Source-1.1.zip
Or read more here.

shadowdancer says
Hi, great tool :)
Is it possible to lauch lazagne against a network target? (LAN)
Thanks
Darknet says
No it’s not, because the credentials are stored locally on the machine. You’d have to gain access to the machine with something like SprayWMI on the LAN and run Lazagne via a reverse shell or similar.
shadowdancer says
Thanks for the tip ;)
Steven says
Great tool thanks!
does it work on the “non running system”?
like if I dual boot a Windows machine on linux to extract saved passwords?
thanks
Darknet says
It potentially could, I honestly don’t know though. Definitely worth a try, as long as the Windows partition is mounted within the Linux OS.