So Twitter exploded earlier with calls of a remote code execution WinRAR vulnerability leaving half a BILLION users open for some hardcore exploitation.
I got interested (obviously..as that’s what I do here) and went to read about it, I have to call pretty sketchy, non-technical reporting from the The Register for once, it seems like it was written by an intern.
To summarise the news…shocker, executing an executable leads to code execution – yah really, no shit?
The fact that it allows you to download a file from the SFX (Self Extracting RAR files basically) panel and execute that, that’s a little shady, but you’ve already executed the .exe self unpacking file..so if it’s from a dubious source, you kinda deserve whatever happens from there on in.
Half a billion users are at risk from a public zero day remote code execution exploit affecting all versions of the popular WinRAR compression software.
A proof-of-concept exploit has been published. Its creator reckons it works on all versions of WinRAR, making it very likely that it will be used by criminals in phishing attacks. WinRAR has been a popular shareware unzipping tool for Windows users over the last two decades. It is plugged heavily thanks to many reviews by software download sites like CNET and Softpedia.
Iranian researcher Mohammad Reza Espargham reported the hole to the Full Disclosure security mailing list.
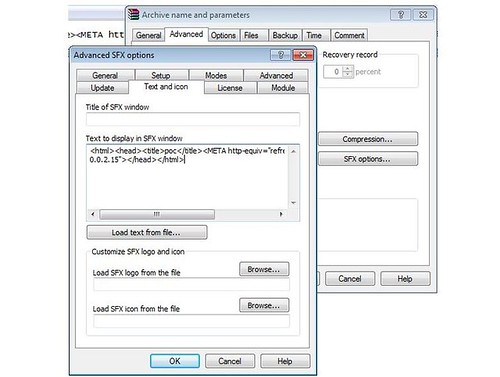
“The vulnerability allows unauthorised remote attackers to execute system specific code to compromise a target system,” Espargham says. “The issue is located in the text and icon function of the ‘text to display in SFX’ window module.”
“Remote attackers are able to generate [their] own compressed archives with malicious payloads to execute system specific codes for compromise.”
Now if this trick worked when opening a .rar file with WinRAR, I’d say that could be a serious problem. But only for SFX (self extracting executable archive) files – not an issue really.
You can watch the PoC of the ‘exploit’ here.
I’m honestly surprised all the major sites are reporting on this like it’s a big thing. Did anyone stop and actually read what’s happening here?
Espargham puts the severity score at 9.2 since it requires a low competency to exploit and requires that users only open the file. Torrent files for games and applications would be a nice attack vector given attacks could be made stealthy.
The vulnerability has not yet received a CVE number by which major bugs are tracked and scored. Users could be owned if the decompress malicious SFX files. Attackers can write HTML code to WinRAR’s window that will run on a target machine when the archive is opened.
MalwareBytes researcher Pieter Arntz says the proof of concept needs subtle tweaking out of the tin for it to work properly. “The proof-of-concept requires some trivial changes before I got it to work,” Arntz says, but that might have been down to a Perl version conflict.
And honestly, why is anyone still using WinRAR since 7zip came out? There’s no excuse at all.
I’m not really surprised this has no CVE, and honestly don’t really expect it to get one. Might WinRAR fix this hole? Probably not, as it’s how SFX works. Why go to such trouble when you could bind malware directly to the SFX archive and have that execute.
Is it serious?
NO.
Source: The Register

R-73eN says
This vulnerability got too much fame. I found it and this mohmamadd is a total script kiddie who copied it.
You can verify by the dates exploits got posted
My exploit
http://0day.today/exploit/description/24292 posted on 25/09/2015
Same exploit
http://0day.today/exploit/description/24296 posted on 26/09/2015
This is copy pasted exploit but written in perl.
Here is a good vulnerability. Without SFX archiving and can be executed remotely without user interaction.
https://www.exploit-db.com/exploits/38361/
Thanks
R-73eN
Darknet says
Yup, verified yours was first, but not that it was the original. Also..his PERL code didn’t even work properly The second one looks interesting, thanks for sharing.
Chris says
The Register article was rewritten after it was reviewed by an editor. Software has design flaws, journalists get things wrong. Fix, learn, move on.
C.
AP says
WinRAR has a superior command-line interface to 7-zip and was much easier for me to script things with.
Welp. That’s it. That’s the only reason to keep using it. 7-zip creates smaller archives and is Libre/Free.
I stopped using WinRAR years ago.
Scripting finds a way.
anon says
WinRAR can add a recovery record that protects against bit flips on disk. They happen all the time, nobody notices.
Xylitol says
http://www.rarlab.com/vuln_sfx_html.htm
http://www.rarlab.com/vuln_sfx_html2.htm
Steve says
Well done. Few sites that eagerly rushed to spread this FUD without fact-checking (which they never do anyway) have bothered to admit their fault. Some have shamelessly and silently modified their articles, or simply added a small note at the end, or made articles/forum threads disappear. I’m especially disappointed with MalwareBytes, which I consider to be a decent program but whose researchers apparently also thought this was some big earth-shattering vulnerability/exploit. Interestingly the forum thread where they were commenting so sagely yet cluelessly on this has disappeared without a trace now.
On top of all this R-73eN’s claim, which seems accurate, shows that this Iranian ‘researcher’ is dumber than I suspected ever since I saw his YouTube video detailing this amazing ‘exploit’.
On an unrelated note, I wish all those touting 7-Zip as the ultimate solution would just zip it (pun fully intended). It is a wonderful archiver no doubt, FOSS to boot. However WinRAR still beats it in *my* opinion when it comes to UI, command line abilities as well as certain split volume related features. Also since I like to compare regularly, I can attest that it’s hardly a certainty that a 7z archive will be smaller than an RAR of the same data. Sometimes 7z wins, sometimes RAR4, sometimes RAR5 and on some rare puzzling occasions sometimes even good ol’ ZIP with its puny dictionary! Truth really is stranger than fiction. All in all, I never could understand this fetish some people have with forcing their own choices down other people’s throats. If you hate commercial software and would die for FOSS, great. That doesn’t mean your program of choice is the best, nor that both cannot be used by those who know better.
Here’s a counterclaim for authorship of the original OLE exploit:
http://www.ghacks.net/2015/10/01/winrar-disclosed-self-extracting-archive-vulnerability-is-none/#comment-3642658
Darknet says
Yah I had a counter-claim too here from someone against R-73eN himself, but the language was so foul and full of ad hominem, I couldn’t let it through. The claim was that other work predated that of R-73eN who is also a ‘n00b skiddie’.
R-73eN says
hello guys.
I never stated that i wrote the OLE exploit.
The OLE exploit was found by a chinese security researcher.
And it was in plain text, and described as OLE RCE, if you read my exploit. But the ms14-064 was just for example since there are 0days for IE every month.
And for the sfx \”vulnerability\” i posted it so the developers of winrar understad that is wrong using the Internet Explorer rendering engine, which they ignored. Then i posted about the Registration reminder they still ignored it. So every time there is a 0day for IE, winrar is vulnerable to RCE through MITM.
For a more detailed write up read this
http://www.rarlab.com/vuln_web_html.htm
http://drops.wooyun.org/papers/9470
Thanks