So the recent XcodeGhost iOS Trojan Infection has escalated quickly, an initial estimate of 39 infected apps has rapidly increased to over 4000!
You can see the FireEye announcement here: Protecting Our Customers from XcodeGhost
XCodeGhost is the first instance of the iOS App Store distributing a large number of trojanized apps, the malicious/infected apps steal device and user information and send stolen data to a command and control (CnC) server
The number of XCodeGhost-infected iOS apps, initially pegged at 39, has ballooned to more than 4,000.
The staggering increase was the handiwork of analysis by FireEye researchers who said that the apps were being hosted on the official Apple App Store.
“Immediately after learning of XcodeGhost, FireEye Labs identified more than 4,000 infected apps on the App Store,” FireEye said.
The malicious apps steal device and user information and send stolen data to a command and control (CnC) server [and] also accept remote commands including the ability to open URLs sent by the CnC server.
These URLs can be phishing webpages for stealing credentials, or a link to an enterprise-signed malicious app that can be installed on non-jailbroken devices.
A FireEye spokesman told Vulture South that many of the infected apps were owned by “big Chinese global brands” such as consumer electronics, telcos, and banks.
The Register has asked FireEye for the names of some of the prominent affected apps and will update this story should the information come to hand.
FireEye put the huge increase in the number of discovered apps to fast scanning by its mobile threat prevention platform.
It seems to be heavily linked to China, with the original XcodeGhost author also being Chinese, you can see the code repo here: XcodeGhost
A translation using Google sees the author apologise and say he wrote this as a personal experiment and the original only collects non-personal data like device type, iOS version, language, country, device name and so on.
Apple has continued to exorcise the App Store of malicious apps uploaded in what has been widely considered to be Cupertino’s first big malware attack.
The apps were infected after developers downloaded a copy of the Xcode iOS development tool through a file-sharing service. That package was modified to trojanise apps in a way that passed App Store security checks, and was advertised on popular developer forums as a faster source to download the 3Gb Xcode file.
The success of the XCodeGhost phish is staggering; that some 4,000 apps were hosed indicates that a lot of developers were sucked into what must have been a very well-executed attack by highly capable malefactors.
Veracode principal solutions architect John Smith said that the attack challenged the notion that iOS was safer than Android.
“In recent years it has seemed that the problem of mobile malware was bigger for Android than for iOS,” Smith said.
“The more rigorous testing regime required before an iOS app can be published has always been considered to be the reason for this difference, but in this case it seems to have fallen short.”
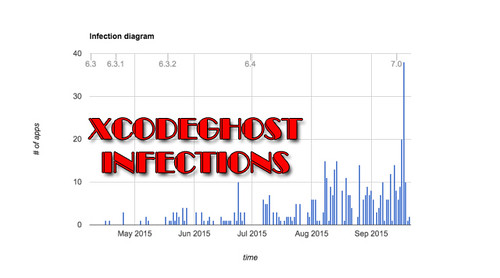
From an infection graph, it seems like it’s been going on for a while, since April 2015 at least – but there’s been a huge peak in infected apps in September.
It’s surprising that such a large number of apps were able to violate Apple’s stringent App Store policies for such an extended period of time.
Even then, it seems like the implementation of XcodeGhost isn’t that malicious and they aren’t sending much more than the original author intended.
Source: The Register
