So no big surprise here but there’s some issues with the default settings in regards to Windows 10 Privacy, if you run through the express install without customizing settings the defaults a little suspect.
A lot of Windows 7 and Windows 8 users have already opted in to the automatic (and free) upgrade to the latest operating system from Microsoft – Windows 10, so I would imagine this effects a lot of people.
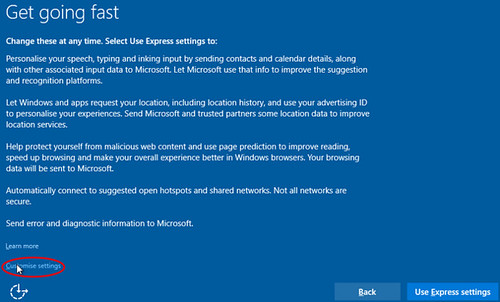
Here’s a quick FYI: if you installed Windows 10, and in a rush to try out Microsoft’s new operating system, you clicked through the default settings without looking, you may want to look again.
If you value your privacy, or have a distrust of Microsoft, you probably want to make sure some or all of the settings are flipped to off. These include things like sending “typing and inking” data to Microsoft’s servers, and letting apps identify you by your unique advertising ID number.
Your physical whereabouts and your web browser history, plus your contacts and calendar records, are also phoned home to Redmond. Your PC will even let other computers download updates from it, and potentially share your Wi-Fi network with strangers.
There’s a handy guide to the settings you need to look out for during the install and afterwards. On an installed system, find the Settings app and select Privacy to see all the controls.
You probably want to turn Cortana off, unless you find it really useful, and don’t forget to opt-out of personalized ads (more info here).
Some of the features, which are on by default, have their uses: for example, SmartScreen is supposed to stop you from downloading malware or visiting websites known to be infecting PCs, assuming you’re using Internet Explorer and apps from the Windows Store. And sending odd-looking executable files to Windows Defender so they can be scanned for malware improves security for everyone using Windows 10.
So yah, no surprise it’s phoning home to Redmond – but the amount of data shared might be more than you are comfortable with, especially coming from Windows 7 (which doesn’t really share anything). I can’t say I’m familiar enough with Windows 8 to comment on its privacy settings or issues.
Here’s the guide to the settings and how to protect yourself – https://fix10.isleaked.com/
But the company tells the press: “Windows does not collect personal information without your consent. To effectively provide Windows as a service, Microsoft gathers some performance, diagnostic and usage information that helps keep Windows and apps running properly. Microsoft uses this information to identify problems and develop fixes.”
Yes, these are interesting features – perhaps even useful. It would be fantastic, though, if there was more information upfront about the services before we decide to enable them, as opposed to forcing them on us and hoping we won’t notice or care. We’re all adults, and we know what it feels like when someone is trying to pull a fast one on us.
And Windows 10 feels like it’s trying to pull a fast one on a lot of us.
Before the Microsoft apologists get too upset, there are similar defaults in OS X and some flavors of Linux. Google Android and Chrome are also pretty aggressive with your data. It always pays to check the default settings.
As mentioned, it’s also not super uncommon and we reported on the Mac OS X Yosemite Spotlight Privacy issue before, Chrome, Android and certain versions of Linux also phone a fair amount of data home.
As always, check the defaults and ensure you choose the settings that protect you to a degree you’re comfortable with.
Source: The Register

Defiant says
That feeling you get, when an article has so many spelling and grammar errors, that it loses credibility.
-“So yah, no surprise it’s phoning how to Redmond”
-“I can’t say I’m familiar enough with Windows 8 to comment on it’s privacy settings or issues.”
Which literally reads:
“I can’t say I’m familiar enough with Windows 8 to comment on IT IS privacy settings or issues.”
Darknet says
Sorry, I was rushing for a flight. Thanks for the corrections :)
Cassie says
This is one of numerous posts I have seen about Windows 10 security settings. I am glad that I don’t use Windows anymore. I feel that Windows should have told its customers about these setting before hand, but the customers are also to blame. We get so used to just trusting what the company says that we don’t ready anything anymore.