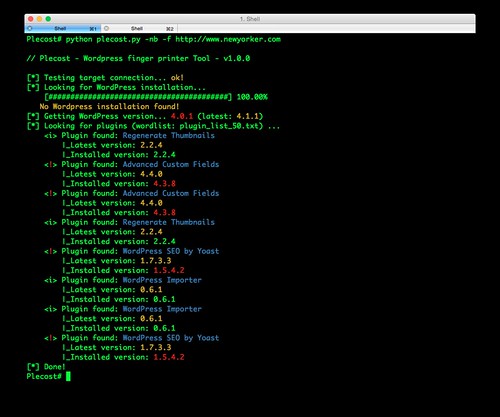
Plecost is a WordPress fingerprinting tool, it can search and retrieve information about the plug-in versions installed in a WordPress installation. It can be used to analyse a single URL or perform an analysis based on the results indexed by Google.
Additionally it also displays the CVE code associated with each plug-in vulnerability, if any exist.
The other tool similar to this is – WPScan – WordPress Security/Vulnerability Scanner. There’s also CMSmap – Content Management System Security Scanner – which has some WordPress functionality.
What’s New?
This Plecost v1.0.1 (major release) has a lot of new features and fixes, like:
- Code rewritten in Python 3.
- Thread support removed, now runs faster & uses less memory with Python 3 asyncio and non-blocking connections.
- Changed CVE update system and storage: Now Plecost get vulnerabilities directly from NIST and create a local SQLite data base with filtered information for WordPress and their plugins.
- WordPress Core vulnerabilities: Now Plecost also manage WordPress Core Vulnerabilities (not only for the plug-ins).
- Add local vulnerability database are queryable. You can consult the vulnerabilities for a concrete WordPress or plug-ins without, using the local database.
- Installation via pip
You can download Plecost here:
Or read more here.

blmvxer says
Something I’ve found with this application is after installing it manually or with pip it doesn’t seem to be able to find the plugin list without actually directing it to the full path.